DFIRVault is an advanced, analyst-driven threat detection and investigation platform built entirely in Splunk. It combines detection engineering, behavior analytics, and investigation workflows into a single operational view for security operations and digital forensics teams.
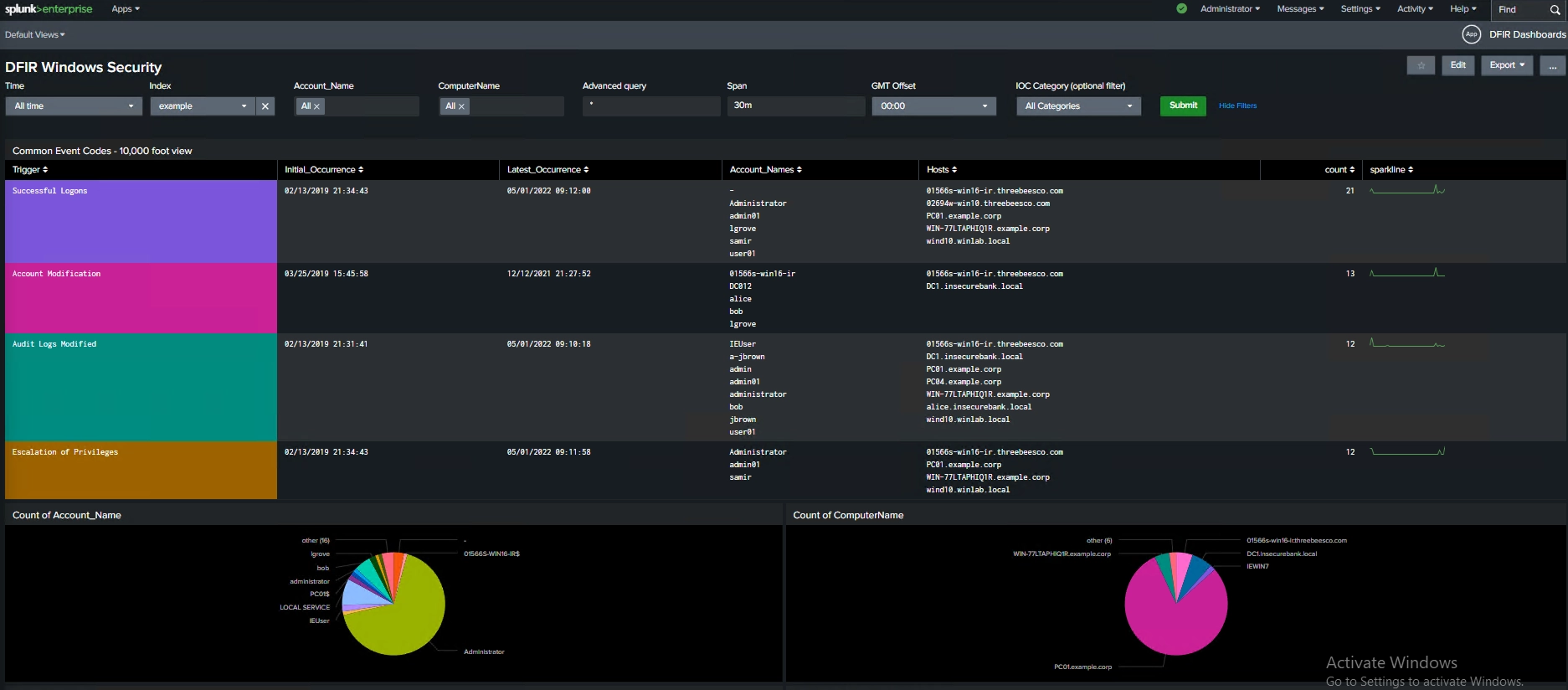
The app ingests Windows security, Sysmon, PowerShell, and endpoint telemetry and automatically enriches events with MITRE ATT&CK techniques, risk scores, kill-chain stages, adversary emulation context, and entity relationships.
DFIRVault goes beyond traditional dashboards by incorporating:
- Risk-based alerting (RBA)
- Peer group and golden image baselining
- Attack path and blast radius inference
- Entity-centric timelines
- MITRE coverage analysis and detection gap identification
- Integrated investigation notebooking
This allows analysts to move seamlessly from detection → triage → scoping → investigation → documentation, all without leaving Splunk.
DFIRVault is designed to be modular, transparent, and extensible — making it suitable for blue teams, DFIR responders, threat hunters, and detection engineers alike.
DFIRVault provides a unified detection and investigation experience across multiple analytical layers:
- Detection & Analytics
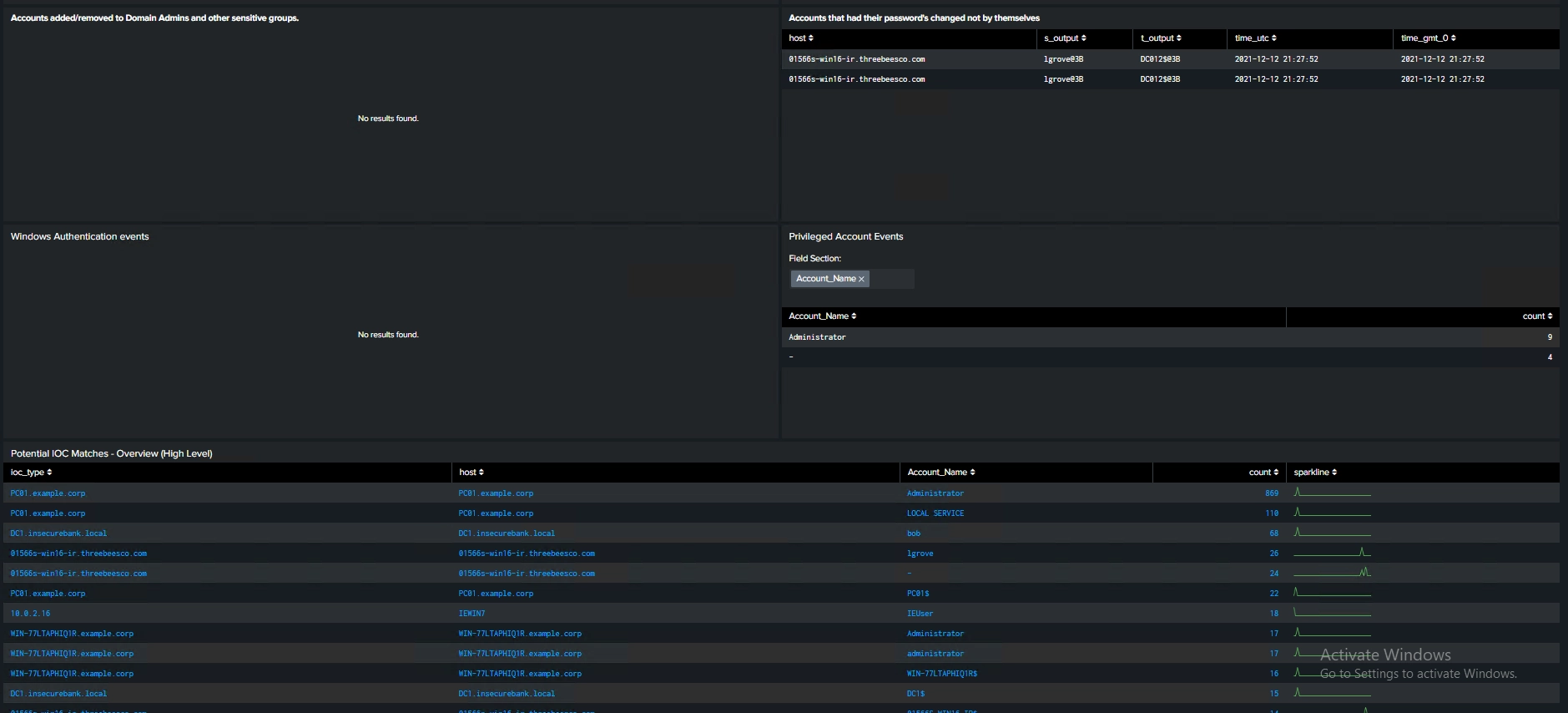
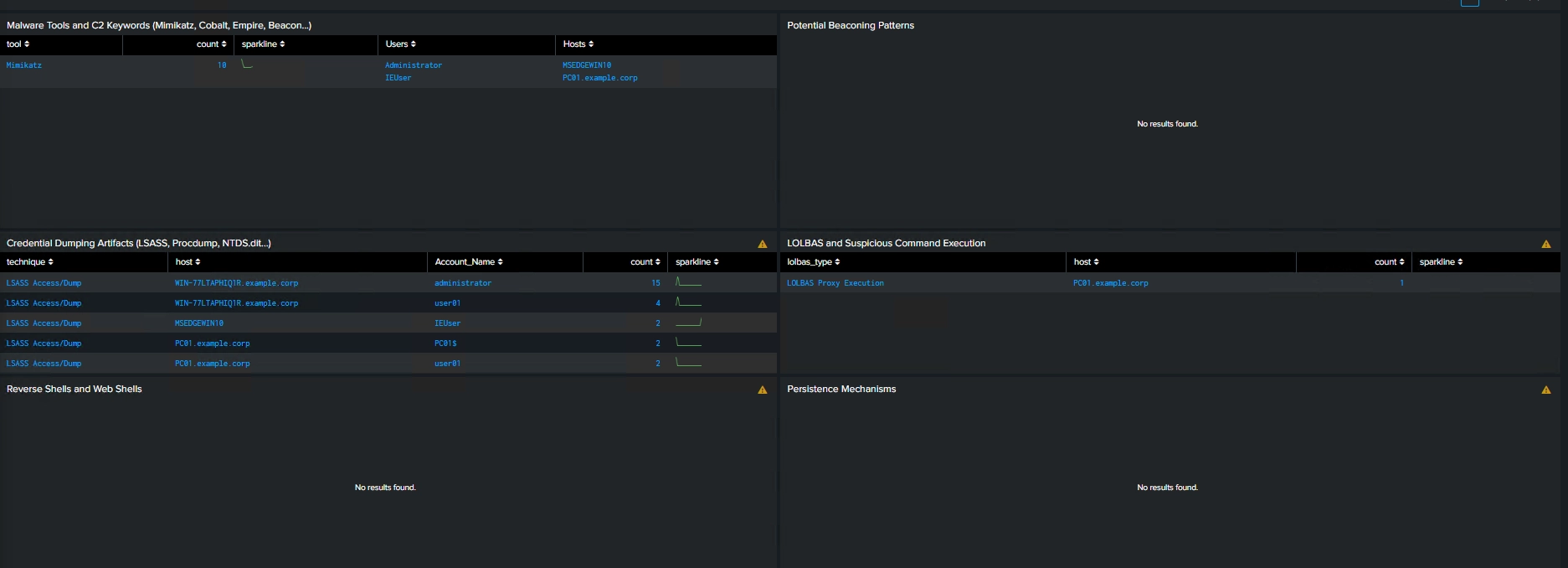
- IOC detection (hashes, IPs, domains, malware tools, C2, ransomware artifacts)
- LOLBAS and living-off-the-land execution detection
- Credential access, lateral movement, persistence, defense evasion, and exfiltration indicators
- Automatic MITRE ATT&CK technique and tactic tagging
- Kill-chain phase classification per event
Behavioral & Risk Analysis
- Risk scoring per event, user, and host
- Risk decay over time
- Automatic suppression for known administrators and service accounts
- Peer group baselining and anomaly detection
- Golden image / baseline drift detection
Threat Modeling
- Attack path inference across entities
- Blast radius estimation based on lateral movement and privilege escalation
- Adversary emulation mapping (MITRE → known threat actors)
- MITRE ATT&CK coverage and gap analysis
Visualization
- Entity timelines per host and user
- Heatmaps for activity density and risk concentration
- Graph visualizations of entity relationships and attack chains
Investigation Workflow
- Entity-centric investigation views
- Built-in notebooking for analyst notes
- Correlation across users, hosts, processes, and network activity
All logic is implemented using Splunk SPL and SimpleXML — no external services or proprietary dependencies required.