







The Trellix (McAfee) ePO Splunk Technology Add-on is designed to collect, normalize, and visualize endpoint security telemetry from Trellix ePolicy Orchestrator (ePO). This section explains how to use the app after installation, including configuration, daily operation, dashboards, and best practices.
The add-on uses Splunk modular inputs to securely connect to the Trellix ePO REST API (and optionally syslog) at scheduled intervals. Retrieved data is parsed, enriched, and normalized to the Splunk Common Information Model (CIM), making it immediately usable for:
Example search:
index=security sourcetype=trellix_epo:threat_events
| stats count by severity, threatName
Example search:
index=security sourcetype=trellix_epo:malware_detections
| stats count by malwareName, host
Example search:
index=security sourcetype=trellix_epo:host_status
| stats latest(datVersion) by host
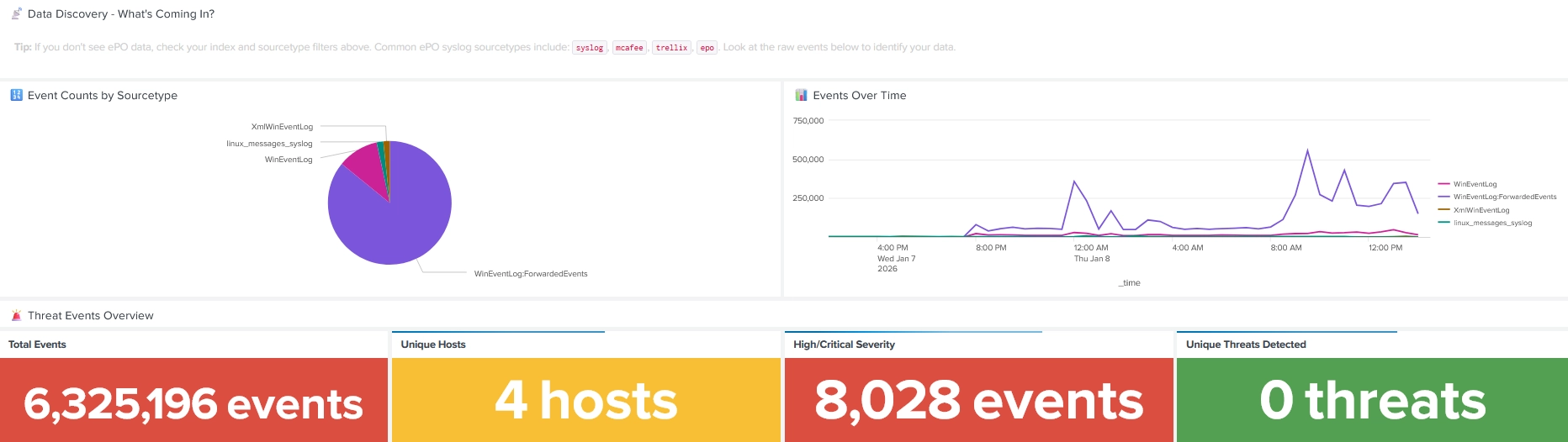
This is the primary dashboard for data collected via the REST API.
Key Use Cases
Main Sections
How to Use
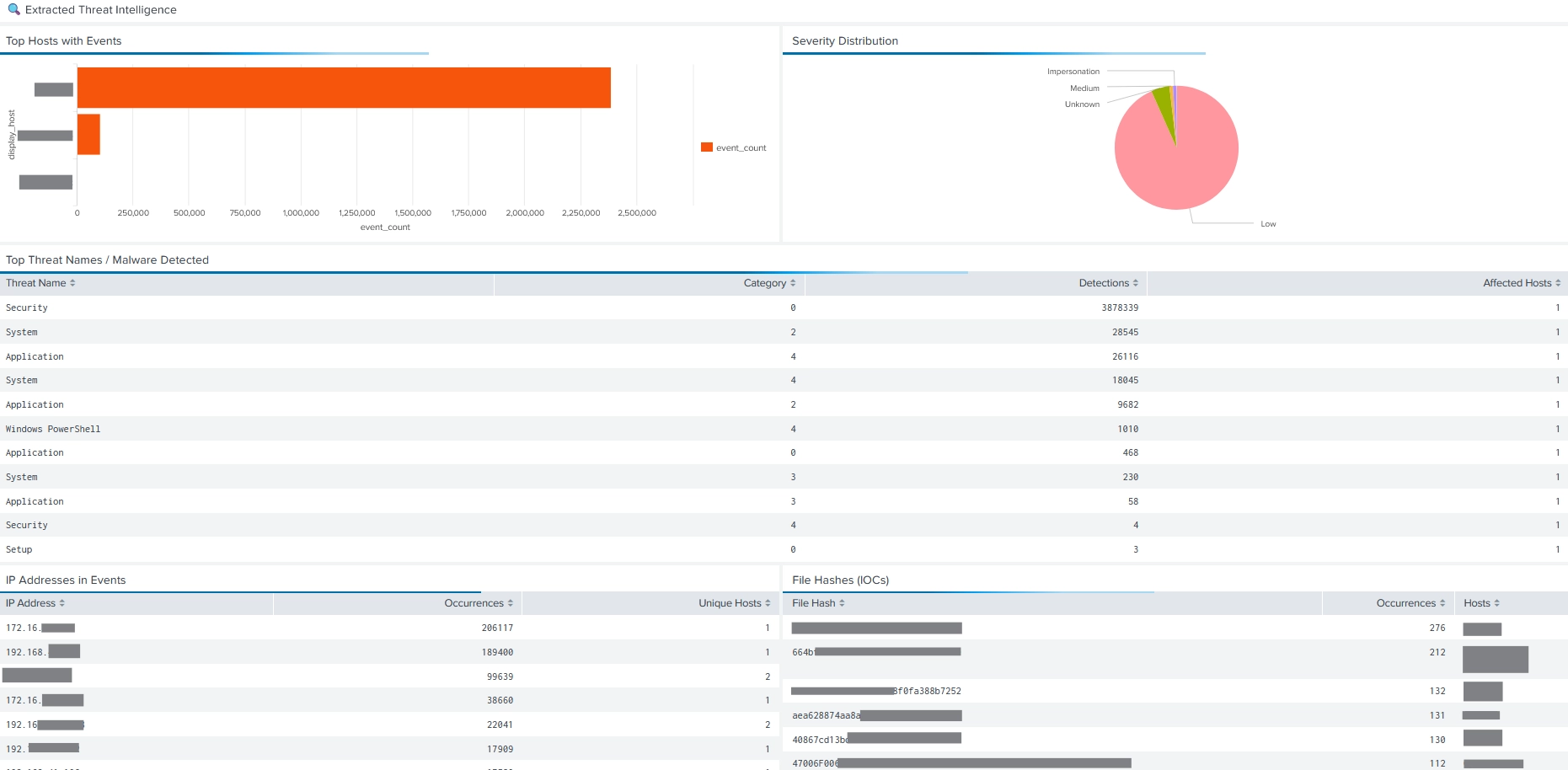
This dashboard is intended for environments where ePO sends threat events via syslog.
Key Use Cases
Usage Notes
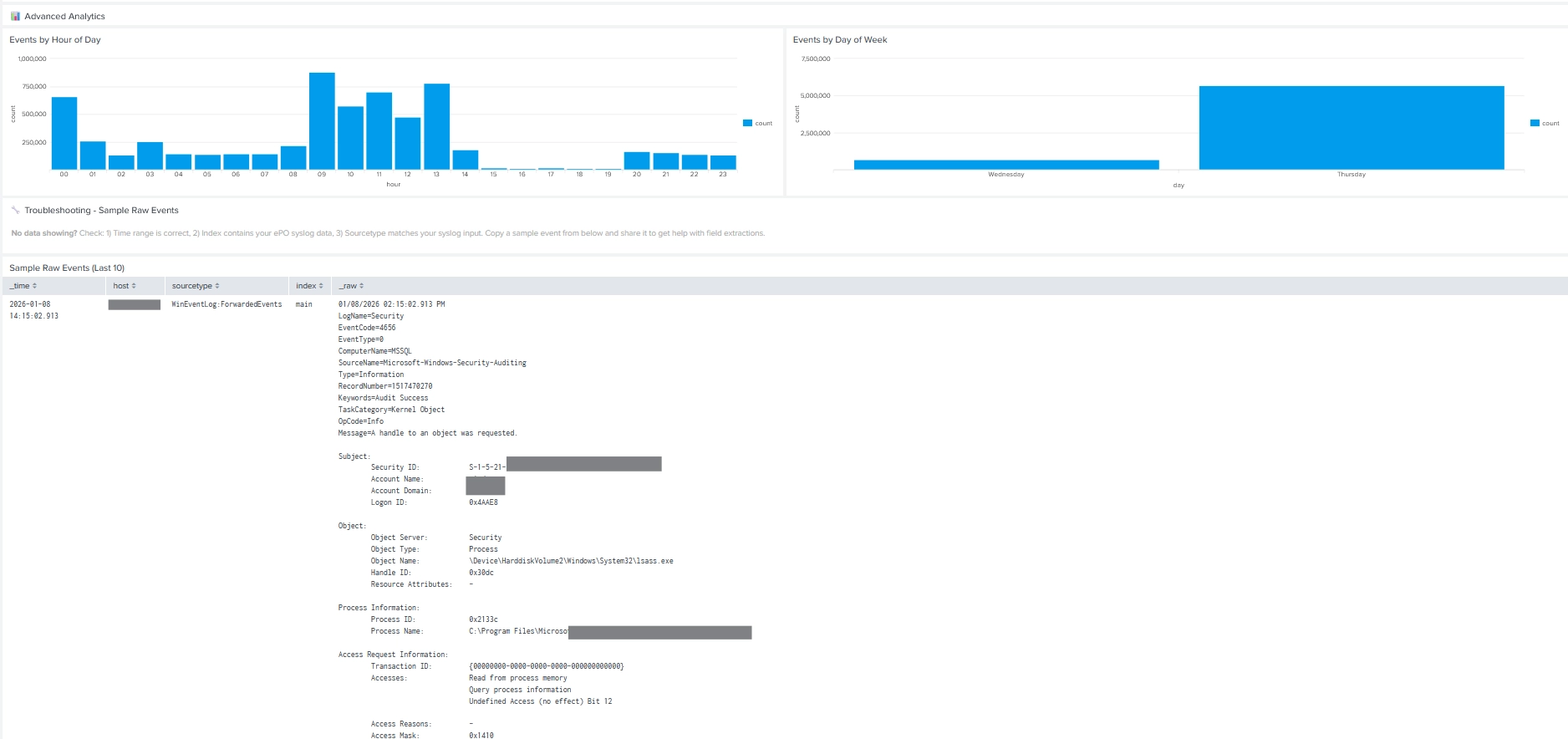
Because all supported data sources are CIM-normalized:
Example CIM-based search:
| datamodel Malware search
| stats count by malware_name, dest_host
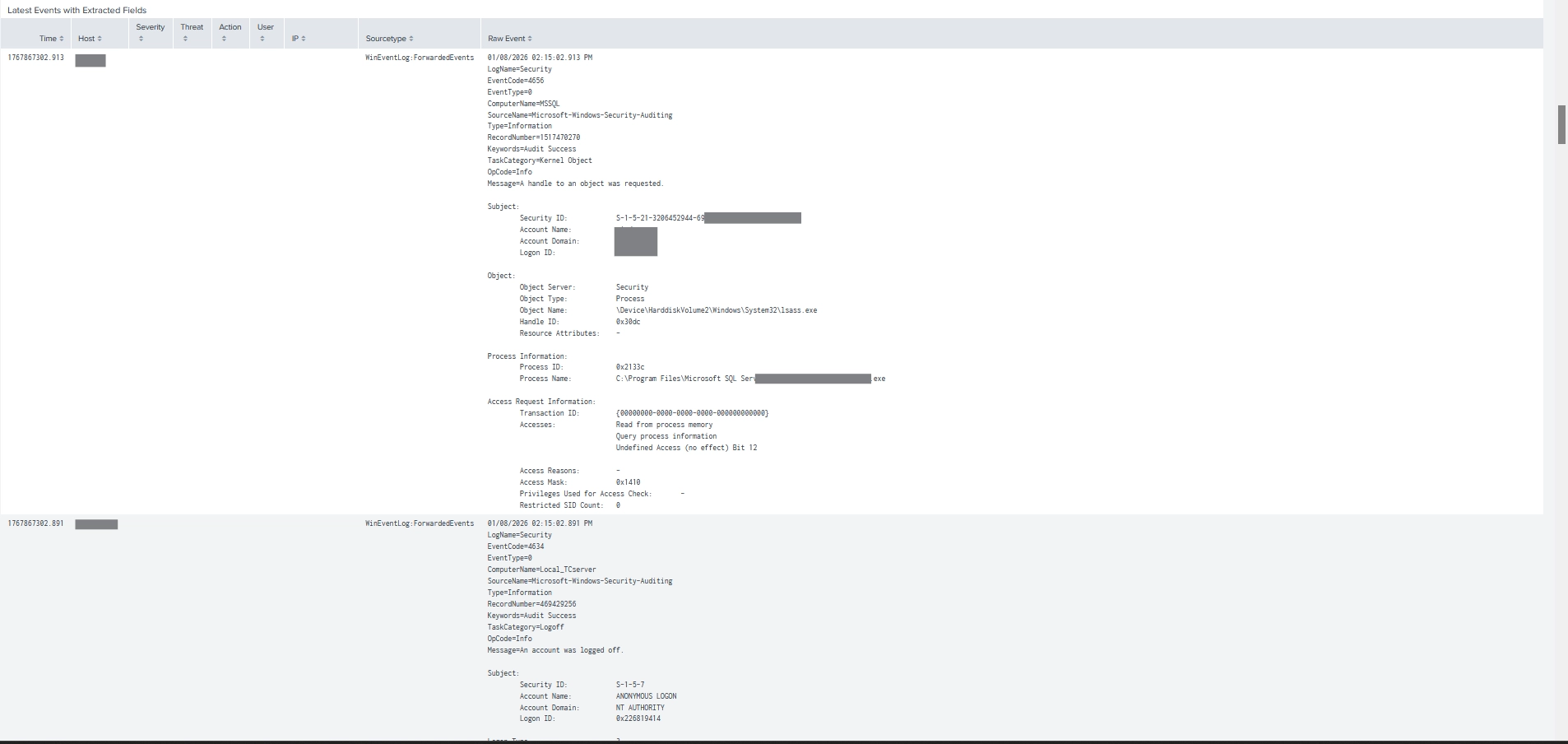
Common alert use cases include:
Example alert search:
index=security sourcetype=trellix_epo:threat_events severity=High
| stats count by host, threatName
By following these usage instructions, users can quickly operationalize Trellix ePO data in Splunk for monitoring, investigation, compliance, and security analytics.
TA-Trellix-EPO Add-on
Release Notes – Version 1.2.2
Release Date: 2026-01-16
Version 1.2.2 focuses on dashboard accuracy, usability, and API reliability. This release corrects multiple dashboard query issues, improves executive visibility, and introduces a critical fix to the Trellix ePO authentication method to prevent intermittent authorization failures.
🔄 Changed
Dashboard Improvements
Switched dashboard theme from dark to light for improved readability and accessibility
Reorganized the Executive Summary to display only metrics backed by actual ingested data:
Total Managed Endpoints
Windows Endpoints
Linux Endpoints
Managed Agents
Events Ingested (last 24 hours)
Authentication Method (Critical Change)
Replaced token-based authentication with HTTP Basic Authentication for all Trellix ePO API requests
Trellix ePO requires username:password basic auth on every request
Eliminated token refresh logic that caused intermittent 401 Unauthorized errors
Now uses requests.auth.HTTPBasicAuth directly
Successfully validated against a production ePO server (201 managed hosts)
🐛 Fixed
Dashboard Query Issues
Fixed timechart span=auto errors
All queries now use span=1h for stability and compatibility
Corrected field name mismatches
Updated all searches to use native ePO fields:
EPOComputerProperties.ComputerName (hostname)
EPOComputerProperties.IPAddress (IP address)
EPOComputerProperties.OSType (operating system)
EPOLeafNode.AgentVersion (agent version)
EPOLeafNode.ManagedState (agent status)
Fixed Agent Status displaying as Unknown
Status is now derived from EPOLeafNode.ManagedState (1 = Managed, 0 = Unmanaged)
Fixed misleading DAT Version visualization
Renamed to Agent Version Distribution
✨ Added
Dashboard Enhancements
Data Source Status panel
Clearly indicates which modular inputs must be enabled for each dashboard section
Section-level notices
Threat Intelligence
Policy Compliance
User Activity
Advanced Analytics
Each section now explains its required data sources
Endpoint Visibility
Added Endpoint Inventory table with:
Hostname
IP address
Operating system
Domain
Logged-in user
Agent version
Last update time
📌 Notes
This release is strongly recommended for all users
Existing credentials remain valid
No data re-indexing required
Splunk restart recommended after upgrade
As a Splunkbase app developer, you will have access to all Splunk development resources and receive a 10GB license to build an app that will help solve use cases for customers all over the world. Splunkbase has 1000+ apps from Splunk, our partners and our community. Find an app for most any data source and user need, or simply create your own with help from our developer portal.