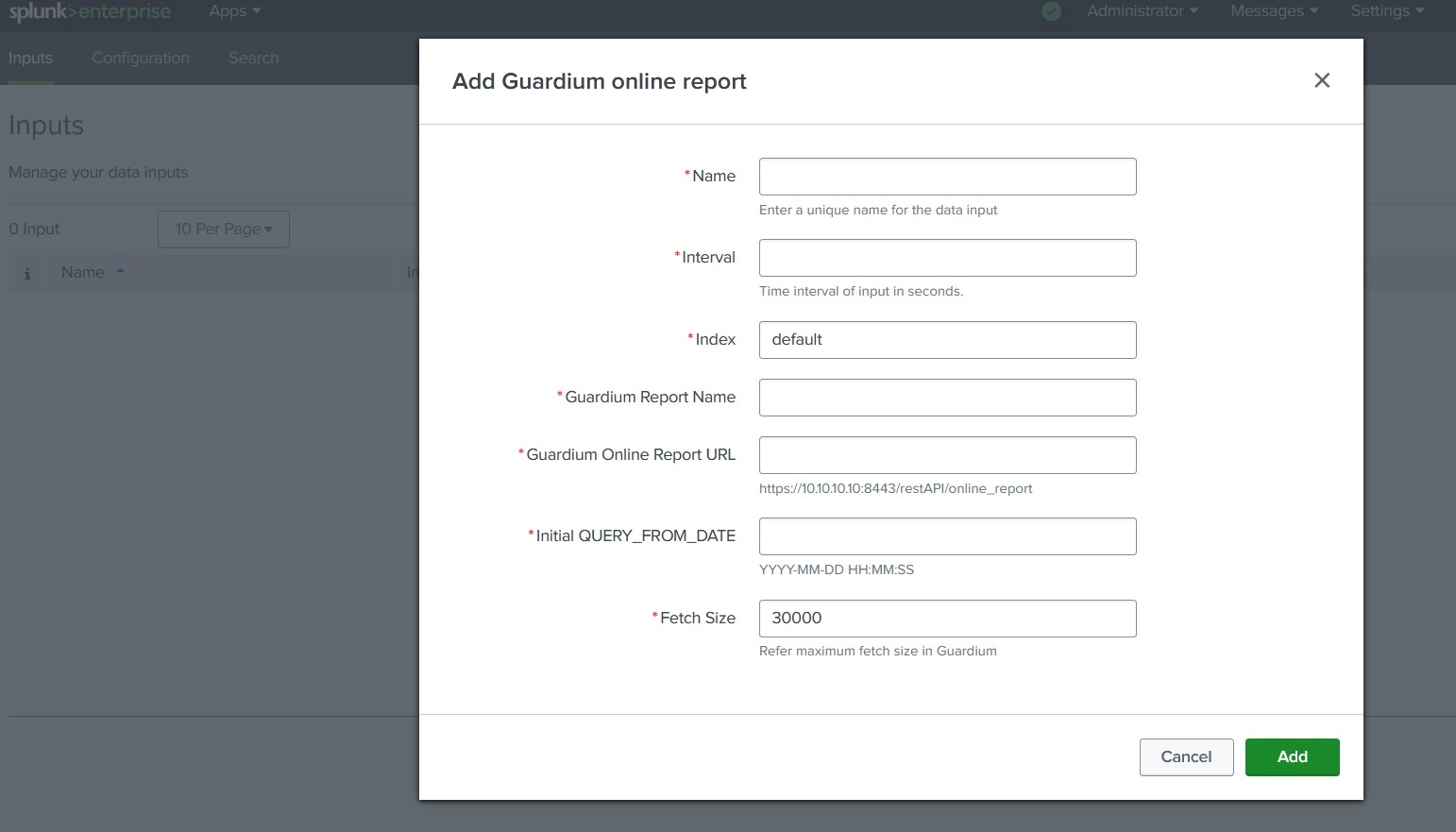
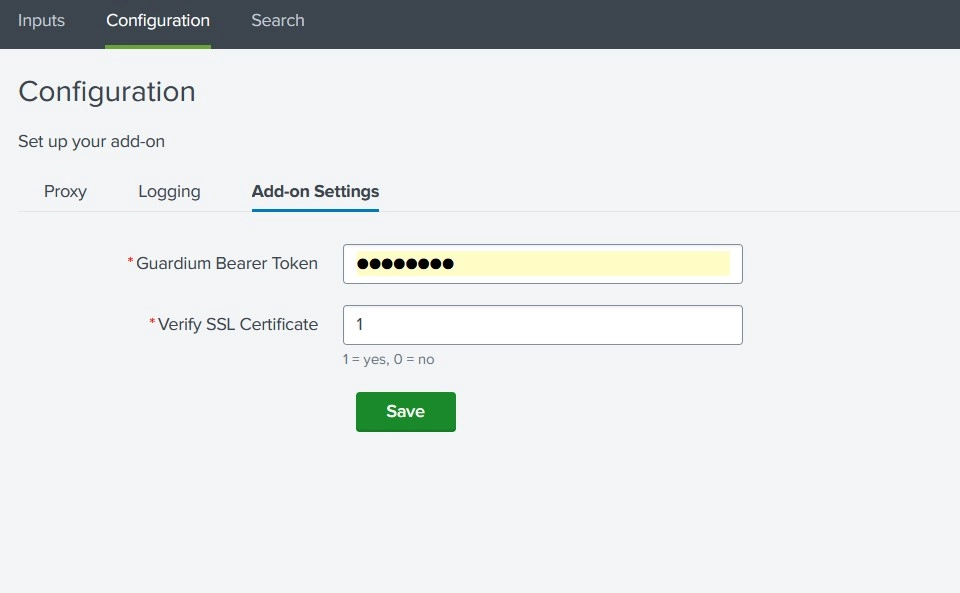




The IBM Guardium REST API Add-on for Splunk collects database audit and SQL activity events from IBM Guardium using the /restAPI/online_report endpoint.
The add-on supports:
- Continuous polling at configurable intervals
- Timestamp-based checkpointing
- Automatic resume after restart
- Scalable data collection using Guardium pagination
- CIM-ready field structure for the Database data model
QUERY_FROM_DATE and QUERY_TO_DATE parameters.Timestamp field.Each input supports the following parameters:
| Parameter | Description |
|---|---|
guardium_url |
Full Guardium REST API endpoint URL |
report_name |
Guardium report name |
initial_from |
Initial start time (YYYY-MM-DD HH:MM:SS) |
fetch_size |
Maximum records per API request |
| Parameter | Description |
|---|---|
auth_token |
Bearer token for Guardium API authentication |
verify_ssl |
SSL verification (1 = enabled, 0 = disabled) |
```bash
curl -k -X POST https://<guardium_host>:8443/restAPI/online_report \
-H "Authorization: Bearer <token>" \
-H "Content-Type: application/json" \
-d '{"reportName":"SQL Activity","indexFrom":"1","fetchSize":30000}'
Key Features:
Runtime checkpointing using timestamps
Automatic retry on next scheduled run
Scalable for large Guardium environments
CIM-ready field structure
Supports multiple Guardium environments via multiple inputs
Secure token-based authentication
JSON-native ingestion
Use Cases:
Database activity monitoring
SQL audit investigations
PCI, SOX, GDPR compliance
Insider threat detection
SOC monitoring and correlation
First release
As a Splunkbase app developer, you will have access to all Splunk development resources and receive a 10GB license to build an app that will help solve use cases for customers all over the world. Splunkbase has 1000+ apps from Splunk, our partners and our community. Find an app for most any data source and user need, or simply create your own with help from our developer portal.