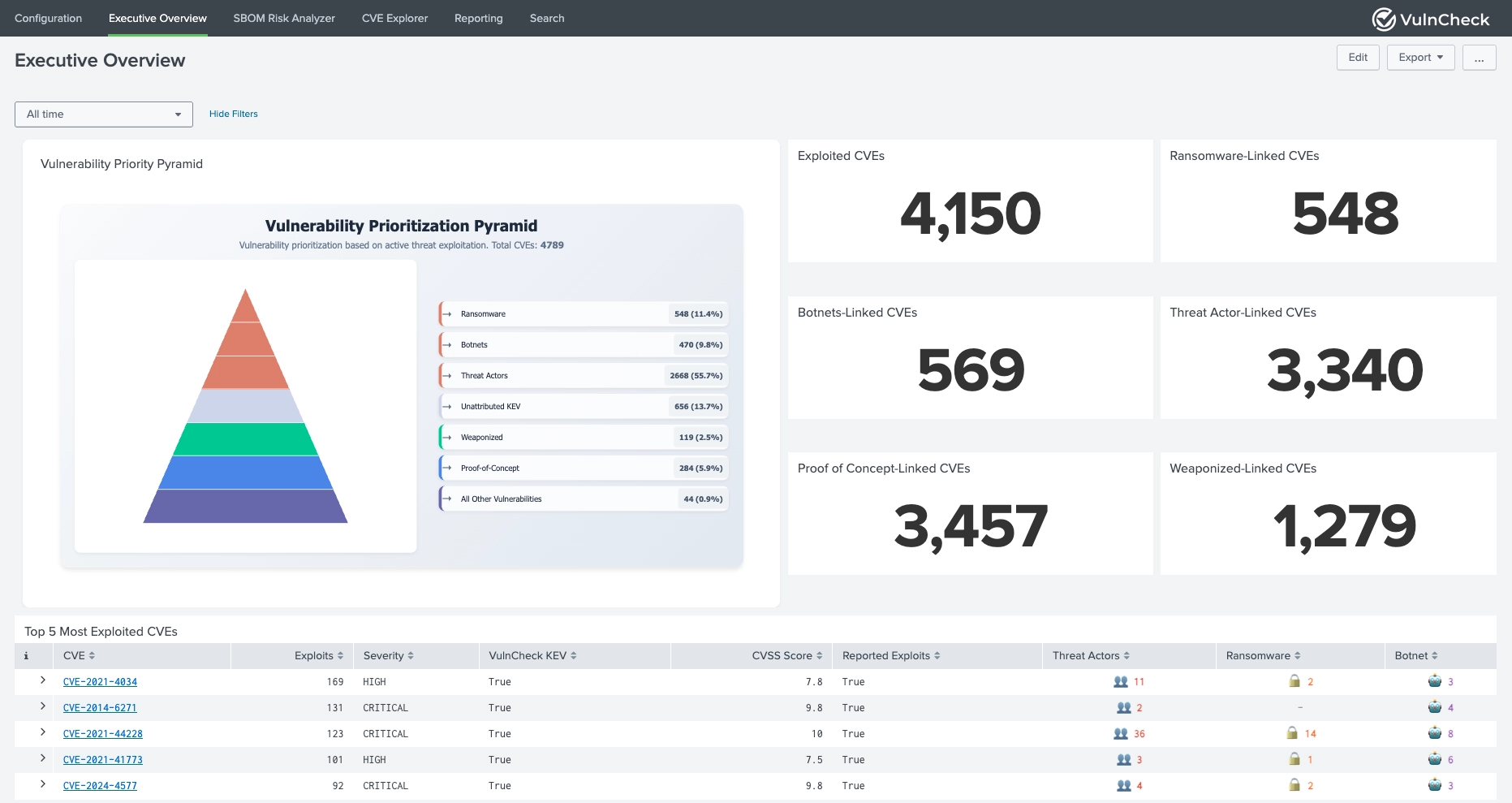
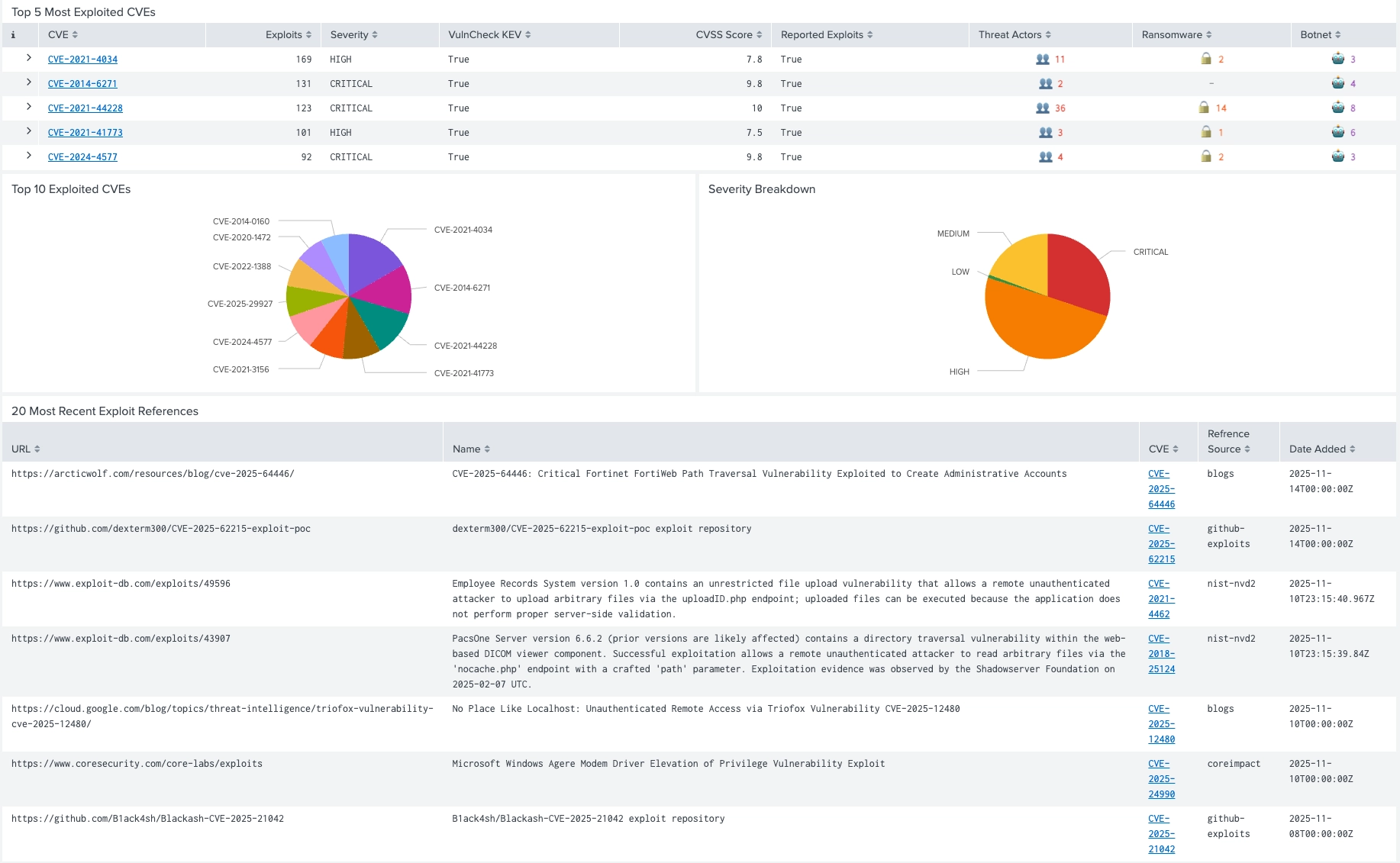
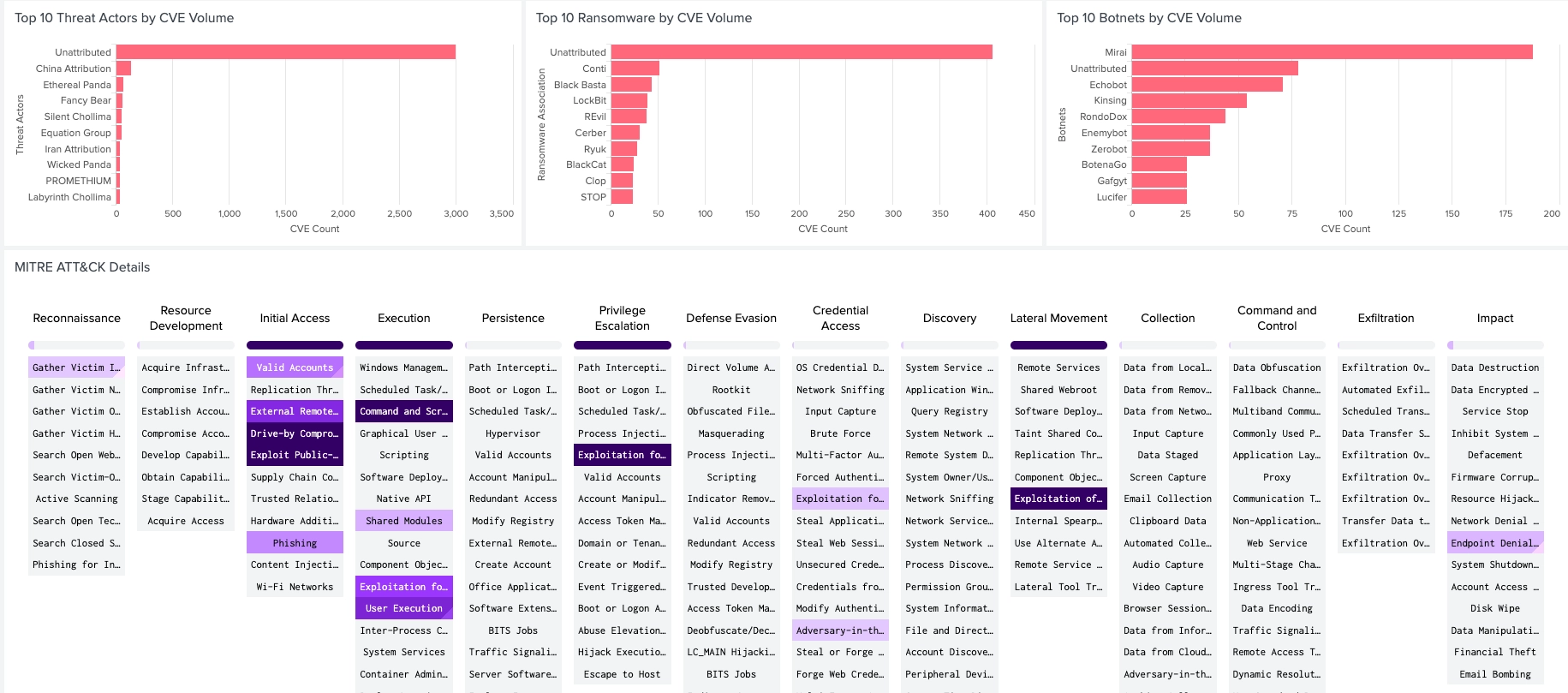
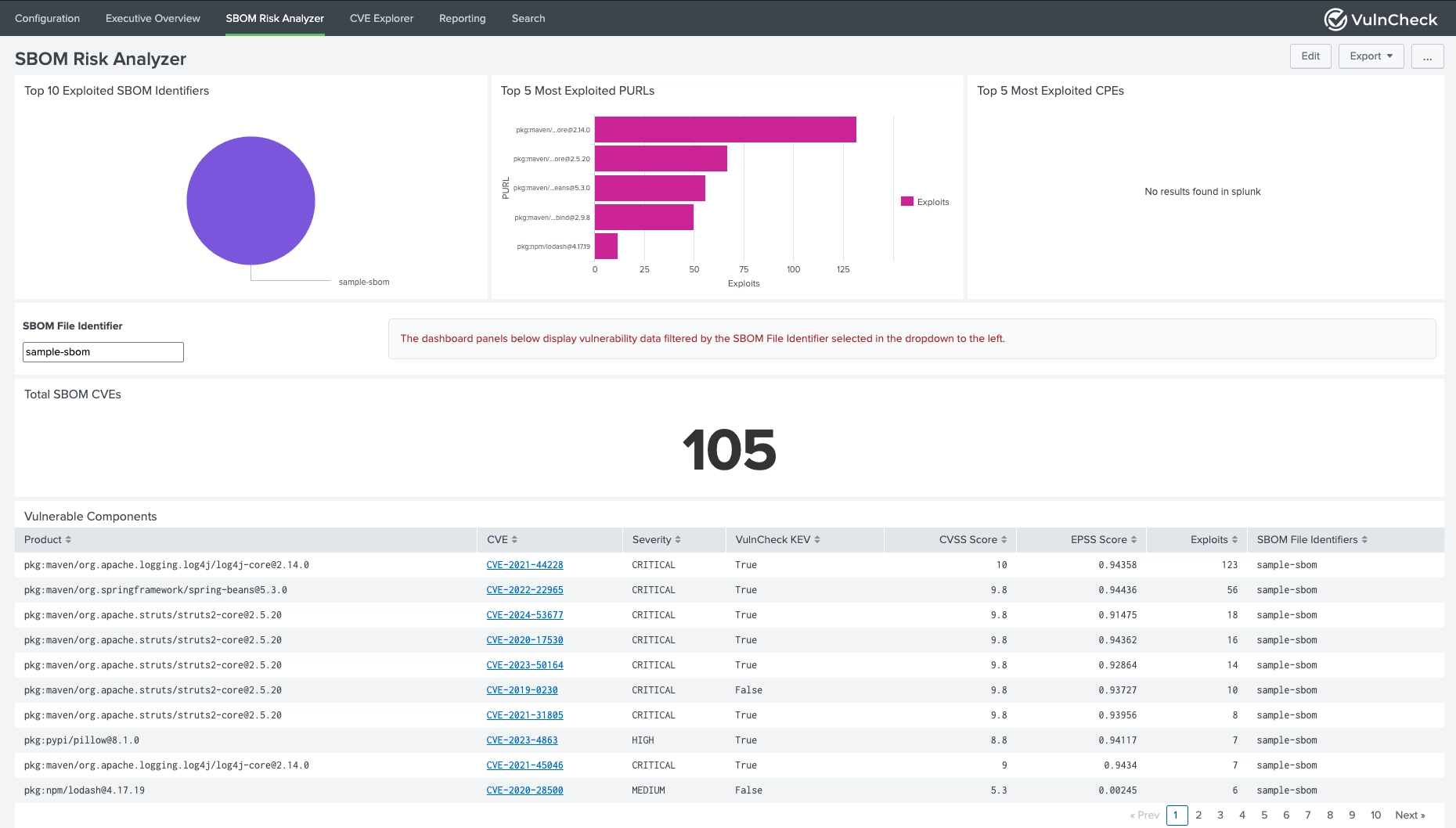
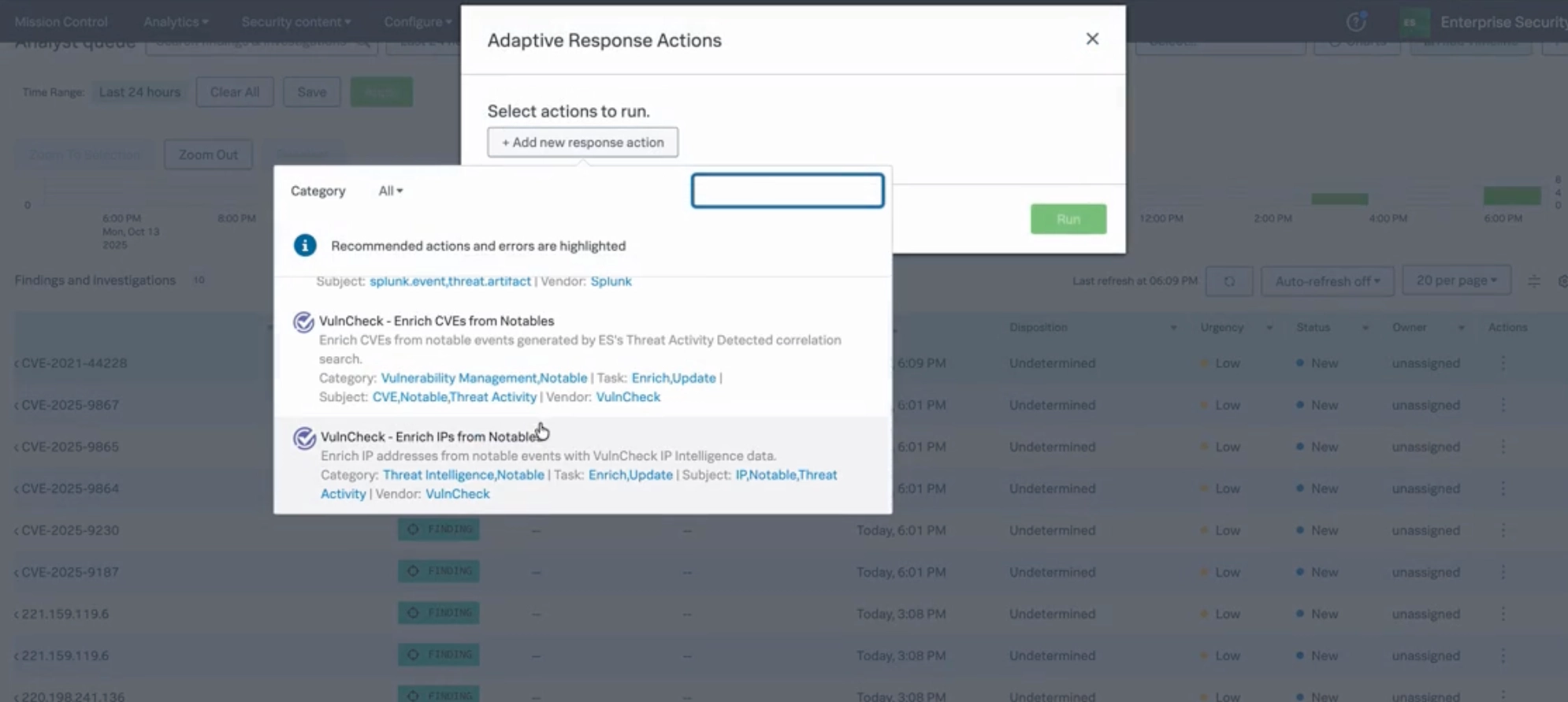










The VulnCheck Exploit Intelligence App for Splunk empowers security teams to enrich CVE data with real-world exploitation intelligence directly inside Splunk. By integrating VulnCheck's comprehensive APIs, the app delivers enriched vulnerability insights, SBOM-driven risk analytics, and threat actor correlation, enabling customers to prioritize vulnerabilities based on active exploitation and real risk, not just static CVSS scores.
| Component | Version/Support |
|---|---|
| Splunk Enterprise | 10.0.x, 9.4.x, 9.3.x, 9.2.x |
| Python Version | Python 3 |
| Operating System | Platform Independent |
| Browser Support | Google Chrome, Mozilla Firefox |
| Deployment Types | Standalone, Distributed, Search Head Clustering, Splunk Cloud |
VulnCheck Exploit Intelligence App for Splunk can be installed through UI as shown below. Alternatively, .tar or .spl file can also be extracted directly into $SPLUNK_HOME/etc/apps/ directory.
Install app from file.Choose file and select the VulnCheck Exploit Intelligence App for Splunk installation file.Upload.| Parameter | Required | Description |
|---|---|---|
| API Key | Yes | Your VulnCheck Premium API key for accessing threat intelligence APIs |
Configure proxy settings if your environment requires proxy access to external APIs.
| Parameter | Required | Description |
|---|---|---|
| Enable | Optional | Check to enable proxy configuration |
| Proxy Type | Optional | HTTP proxy type (default: http) |
| Host | Optional | Proxy server hostname or IP address |
| Port | Optional | Proxy server port |
| Username | Optional | Proxy authentication username |
| Password | Optional | Proxy authentication password |
Configure automated enrichment of vulnerability data from various sources.
| Parameter | Required | Description |
|---|---|---|
| Enable | Optional | Enable/disable enrichment process |
| Enrich Data For | Yes | Select data type (CVEs, PURLs, CPEs) |
| Data Source | Yes | Source type (Index, Lookup, CIM) |
| Index | Conditional | Splunk index for data source |
| Sourcetype | Conditional | Sourcetype for index-based enrichment |
| Field | Conditional | Field containing values to enrich |
| Other Fields | Optional | Additional fields user wants to include in the enriched data from the source. |
| Lookup | Conditional | Lookup to be used for enrichment |
| Column Name | Conditional | Column Name having values to enrich |
| Other Column Names | Optional | Other column names user wants to add in the enriched data from the source |
| Data Model | Static Value | Data model from which the data will be searched and enriched |
| Data Model Field | Static Value | Data Model field that contains the values to enrich |
| Store enrichment details to Index | Optional | Should data be saved in an index? |
| Index | Conditional | The index to save the enriched data |
| Interval | Yes | Enrichment frequency (1H, 4H, 6H, 12H, 24H) |
| Enrich Historical Data | Conditional | Enable to collect historical vulnerability data from a specific timestamp |
| Start Date | Conditional | Date and time from which you want to fetch events. Enter the value in 'YYYY-MM-DDThh:mm:ss' format e.g. 2025-04-17T09:12:36. Time zone will be set to UTC |
Upload and analyze Software Bill of Materials files for vulnerability assessment.
| Parameter | Required | Description |
|---|---|---|
| SBOM File | Yes | Upload SPDX or CycloneDX format file |
| SBOM File Identifier | Yes | Unique identifier for the SBOM file |
| Overwrite existing enriched data for this file | Optional | Replace existing data for same identifier |
| Store enrichment details to Index | Optional | Save enriched data to Splunk index |
| Index | Conditional | The index to save the enriched data |
Perform one-time enrichment of specific CVEs, PURLs, or CPEs.
| Parameter | Required | Description |
|---|---|---|
| Enrich Data For | Yes | Data type (CVEs, PURLs, CPEs) |
| Ad hoc Input Type | Yes | Upload CSV or Add manually |
| CSV File | Conditional | Upload the CSV File here |
| Column Name | Conditional | The Column Name having values to enrich |
| Other Column Name | Conditional | Other columns you want to add in the enriched data from the source |
| Values | Conditional | Comma-separated list of identifiers |
| Store enrichment details to lookup | Optional | Save results to lookup table |
| Store enrichment details to Index | Optional | Save results to Splunk index |
| Index | Conditional | The index to save the enriched data |
As a Splunkbase app developer, you will have access to all Splunk development resources and receive a 10GB license to build an app that will help solve use cases for customers all over the world. Splunkbase has 1000+ apps from Splunk, our partners and our community. Find an app for most any data source and user need, or simply create your own with help from our developer portal.