Real-time, high-confidence threat intelligence from Bitdefender integrated into Splunk.
Gain immediate visibility into novel attacks, malicious infrastructure, and active threat campaigns powered by telemetry from hundreds of millions of protected devices worldwide.
Security teams face a constant challenge: finding the real threats among countless logs and alerts. Many threat intelligence feeds are incomplete, outdated, or rely heavily on honeypots and voluntary submissions, which leaves dangerous gaps in visibility.
Bitdefender Threat Intelligence for Splunk addresses this by providing intelligence built on unique global telemetry from hundreds of millions of endpoints and networks protected across B2B and B2C environments. We detect and analyze threats in real time. When attackers create new infrastructure, deploy new malware, or exploit a vulnerability, we are among the first to know. With this Splunk integration, you can act on that knowledge immediately.
The app ingests Bitdefender’s curated and correlated threat data directly into your Splunk environment, including:
- New indicators discovered in the wild
- Correlated IoCs with attribution to actors and malware families
- Confidence and severity scores to help prioritize security tasks
- Reputation feeds updated within minutes of detection
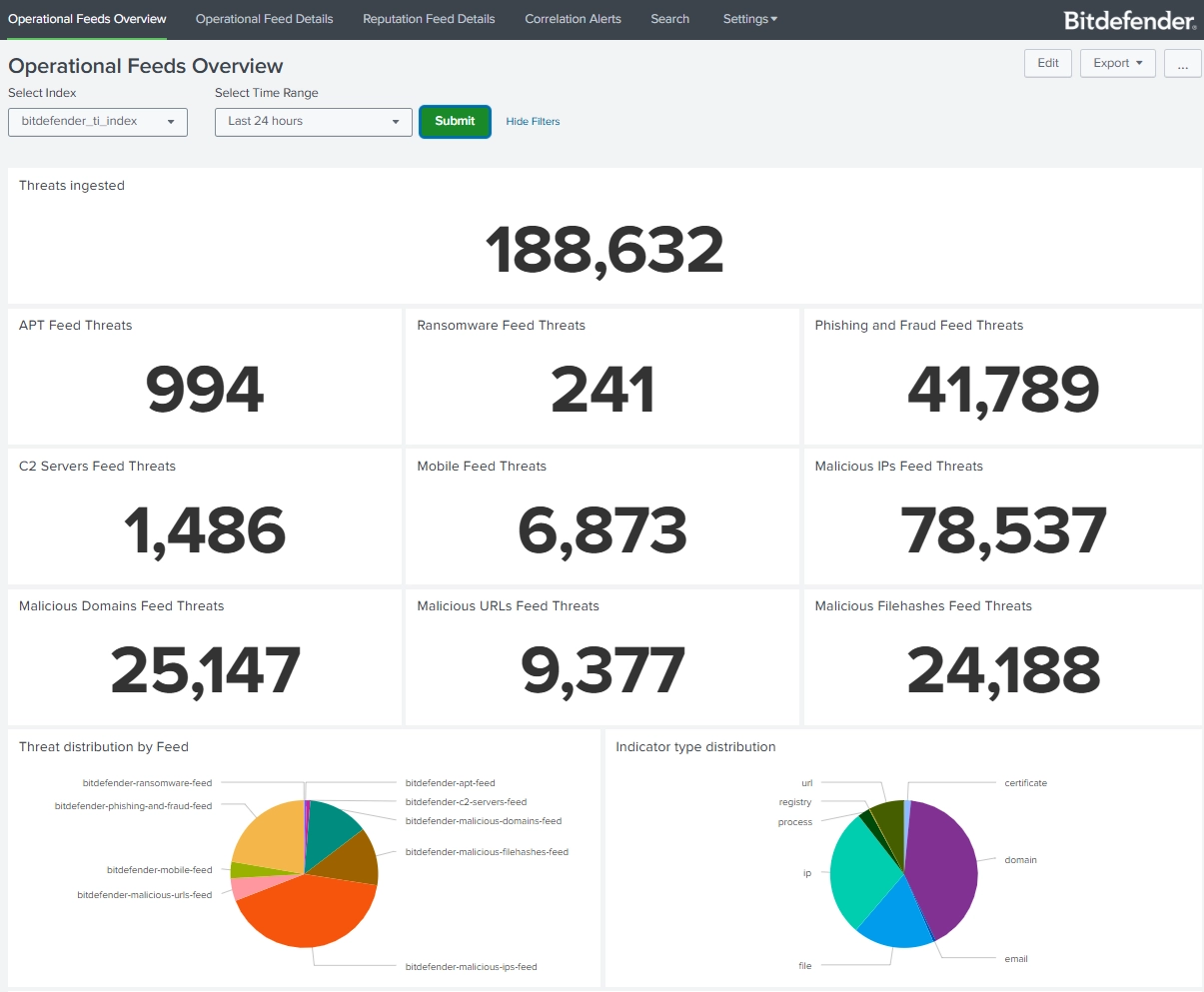
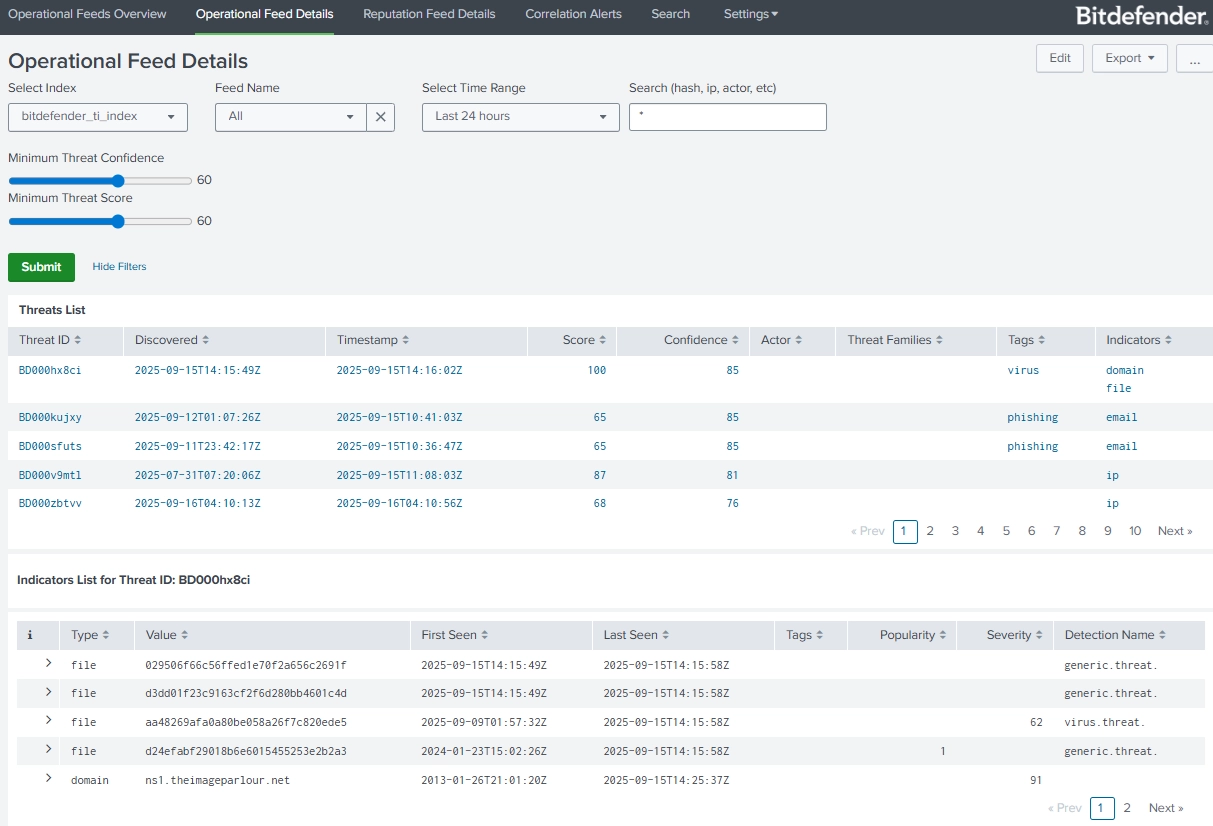
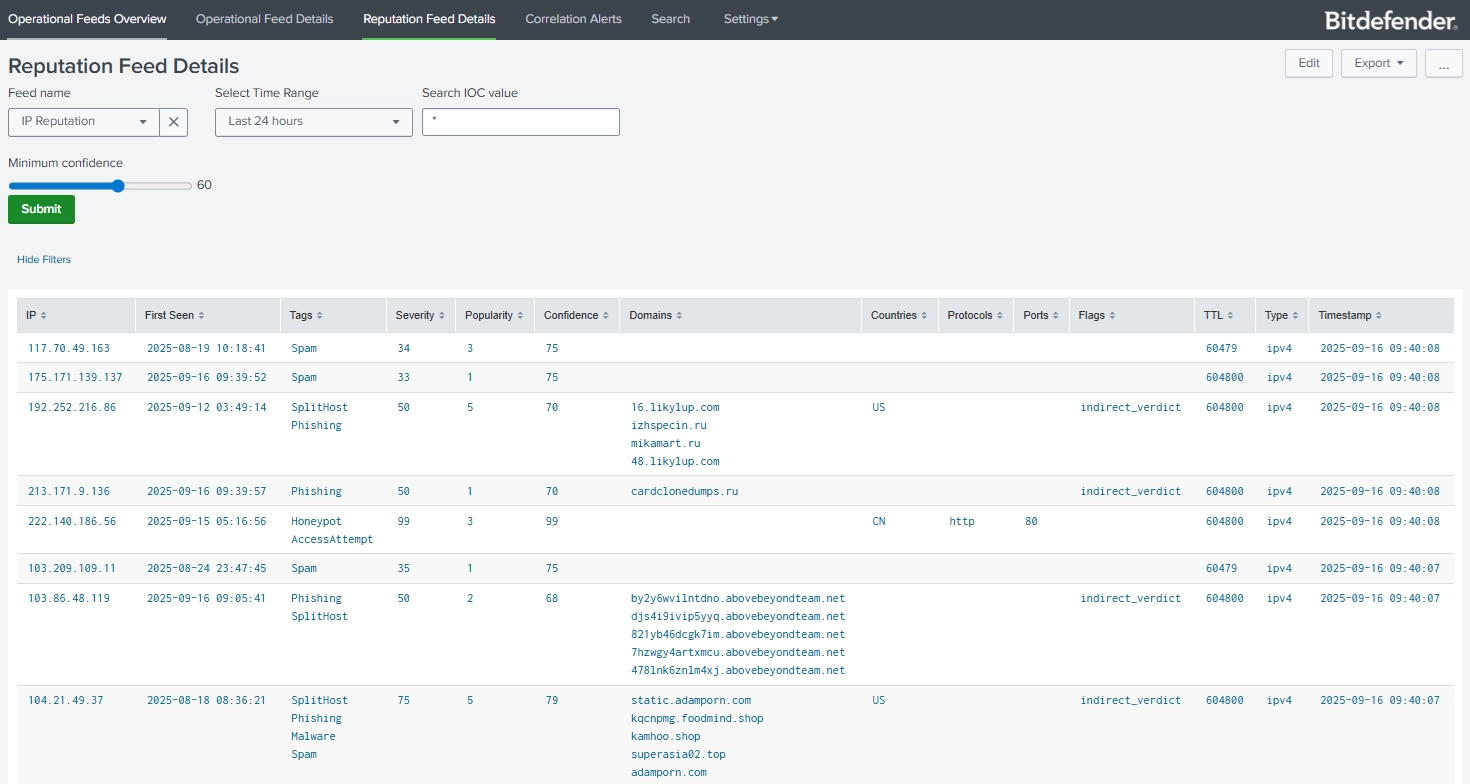
Once in Splunk, you can use the data for lookups and correlation with your internal logs. Prebuilt dashboards such as Operational Feeds Overview, Operational Feed Details, Reputation Feed Details and Correlation Alerts give immediate context on active threats. Integration with Splunk Enterprise Security allows you to create correlation searches and alerts based on your own parameters, enabling faster incident response.
Unlike providers who depend mainly on honeypots or passive data, Bitdefender Threat Intelligence combines honeypots, scrapers, voluntary submissions, and most importantly real-world endpoint data. This ensures our feeds reflect active, ongoing attacks across industries and regions, from fileless malware in corporate networks to generic trojans targeting consumers.
Detections are featured in our feeds in under five minutes from first seen times, offering the actionable context needed to strengthen defenses, speed up investigations, and prepare effective threat hunting exercises.
Data and Intelligence
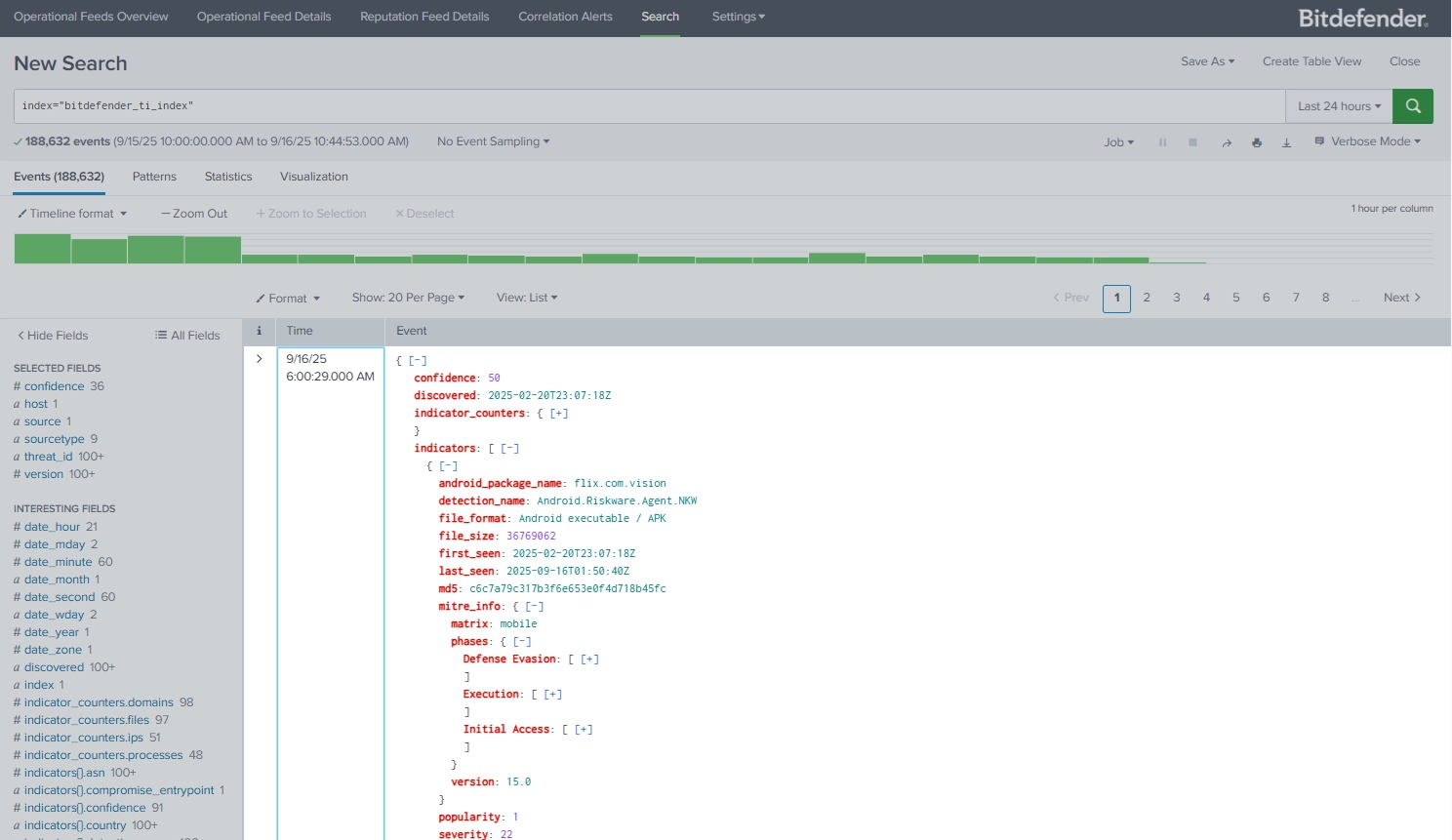
- Real-time ingestion of IoCs (domains, IPs, URLs, file hashes, CVEs)
- Actor and malware family attribution
- Confidence and severity scoring for prioritization
- Novel indicators delivered within minutes of detection
Dashboards and Analytics
- Operational Feeds Overview for high-level visibility
- Operational Feed Details for deep-dive investigations
- Reputation Feed Details to check IoCs that can be correlated with internal data
- Correlation Alerts to view triggered alerts upon IoC matches with TI data
Integration and Usability
- Supports Splunk Enterprise (v9.2.1+) and Splunk Enterprise Security
- Data format parsing for easy use in Splunk dashboards and reports
- Simple API key configuration with selectable feeds
- Quick deployment via Splunkbase or local file install
Start your free trial today and turn global threat visibility into clear, timely security action within Splunk.