







Cyber Security Essentials is a must-have Splunk app for organizations looking to enhance threat detection beyond traditional indicators of compromise (IOCs). The app focuses on detecting advanced persistent threats (APTs), state-sponsored attackers, and various types of malware by analyzing patterns and behaviors in your organization's assets. It also maps threats to the MITRE ATT&CK framework, providing additional context and improving threat intelligence alignment.
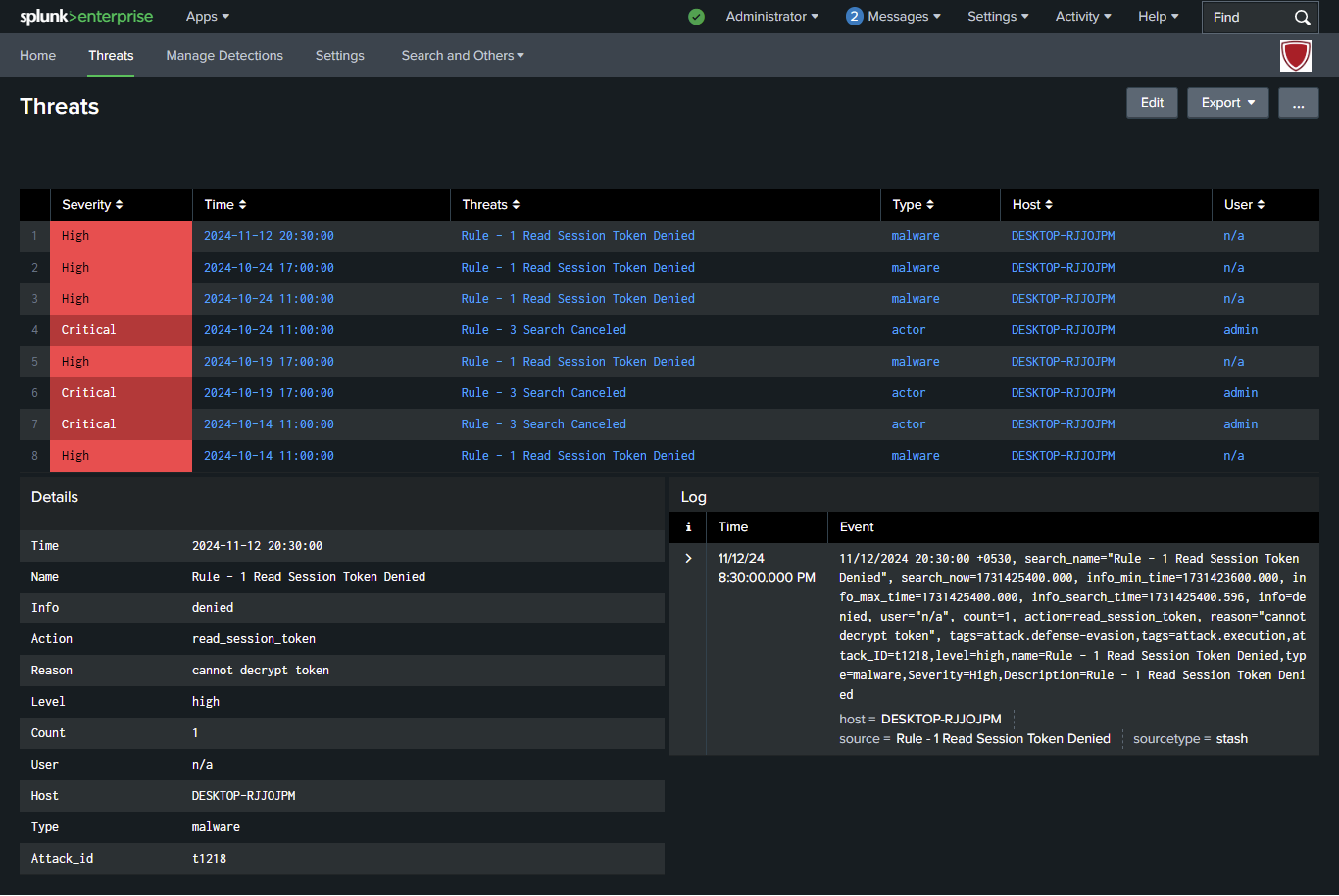
Detection of Advanced Persistent Threats (APTs) and State-Sponsored Attackers: Cyber Security Essentials is tailored for identifying sophisticated threats that often bypass traditional defenses. By using advanced threat hunting queries, it goes beyond basic IOC matching to detect behaviors consistent with APTs and other advanced attackers.
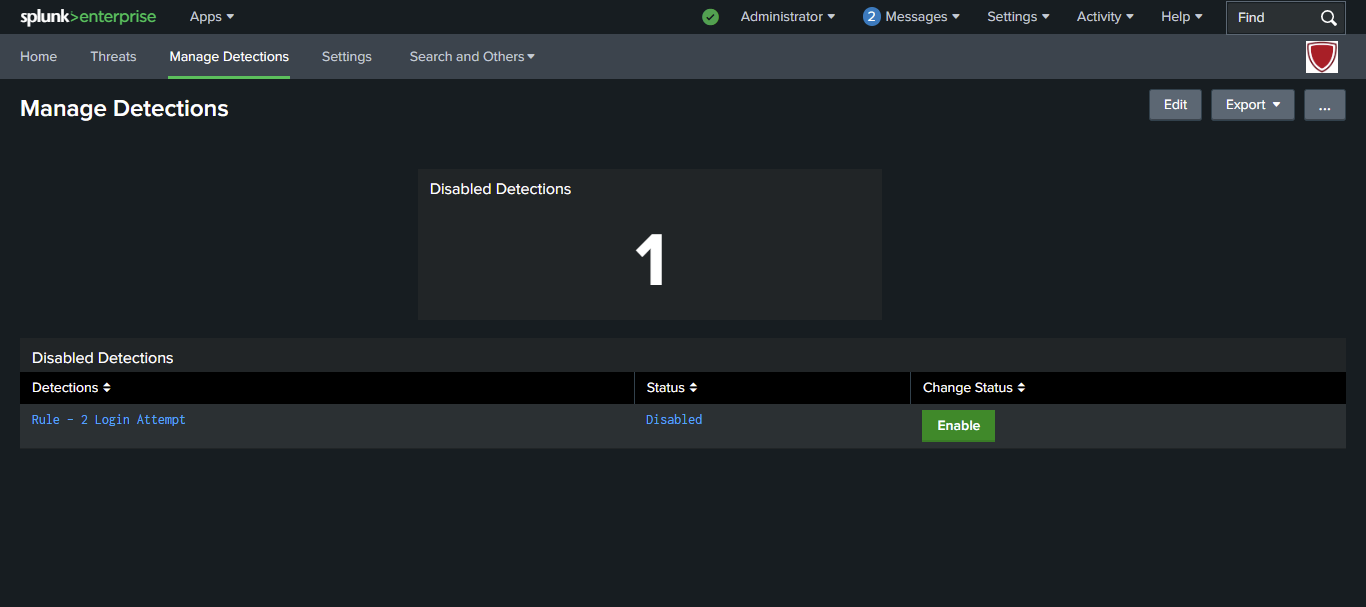
The app maps detected threats to the MITRE ATT&CK framework, providing security teams with insights into the tactics and techniques used by attackers. This mapping makes it easier to understand, track, and mitigate advanced threats.
Cyber Security Essentials uses threat hunting queries that incorporate regular expressions and advanced analytics, allowing it to detect patterns indicative of cyber threats even when threat actors frequently change IPs, hashes, or other basic indicators.
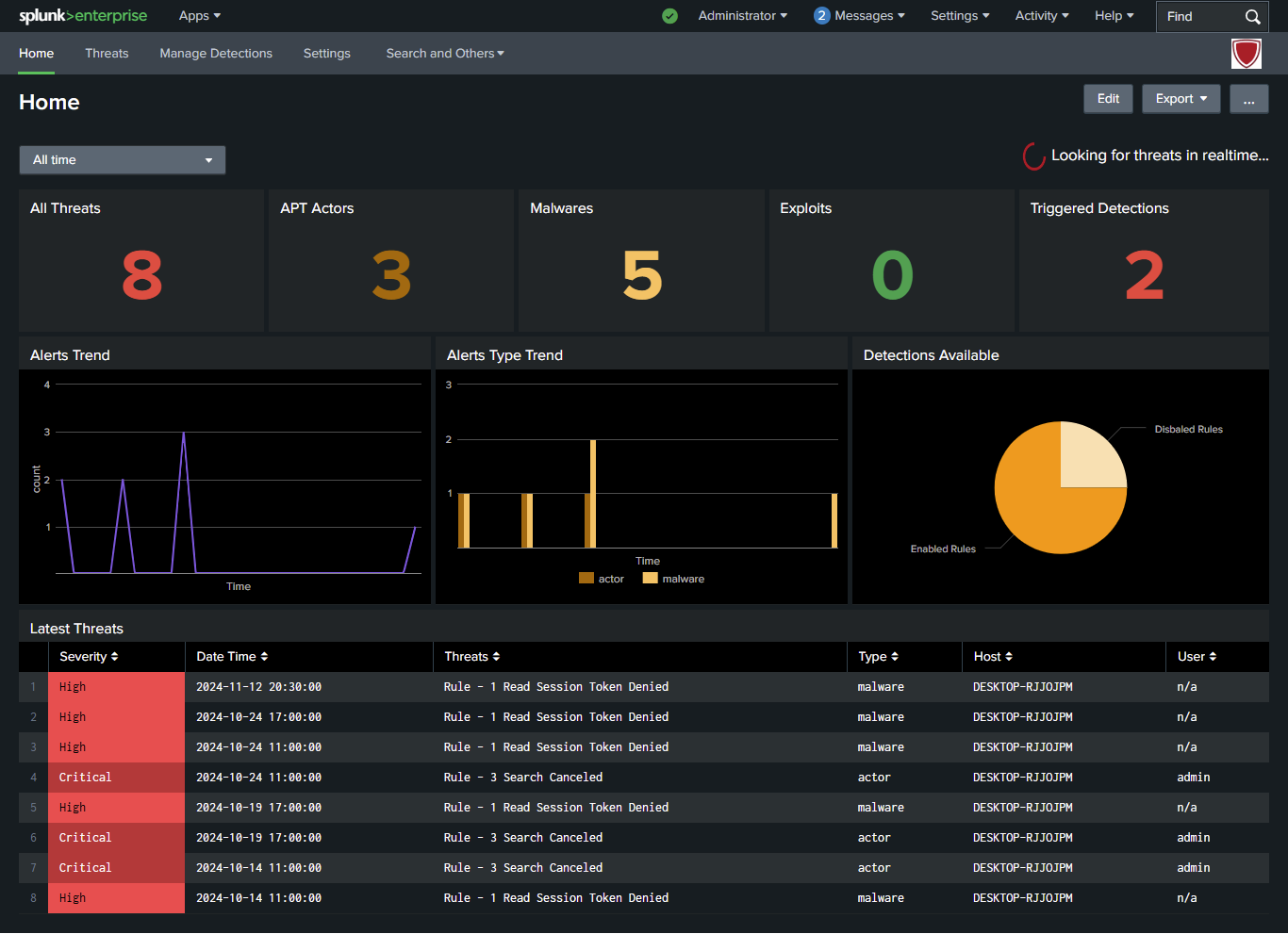
The app’s real-time monitoring capabilities allow it to identify malicious activity as it happens, providing immediate alerts for faster response.
Cyber Security Essentials is ideal for organizations that require a proactive approach to detecting complex cyber threats. By leveraging behavioral analysis and mapping to MITRE ATT&CK, the app provides insights into the tactics used by adversaries, helping organizations understand and respond to threats more effectively. Its advanced detection methods allow security teams to stay ahead of attackers, even as tactics and techniques evolve.
As a Splunkbase app developer, you will have access to all Splunk development resources and receive a 10GB license to build an app that will help solve use cases for customers all over the world. Splunkbase has 1000+ apps from Splunk, our partners and our community. Find an app for most any data source and user need, or simply create your own with help from our developer portal.