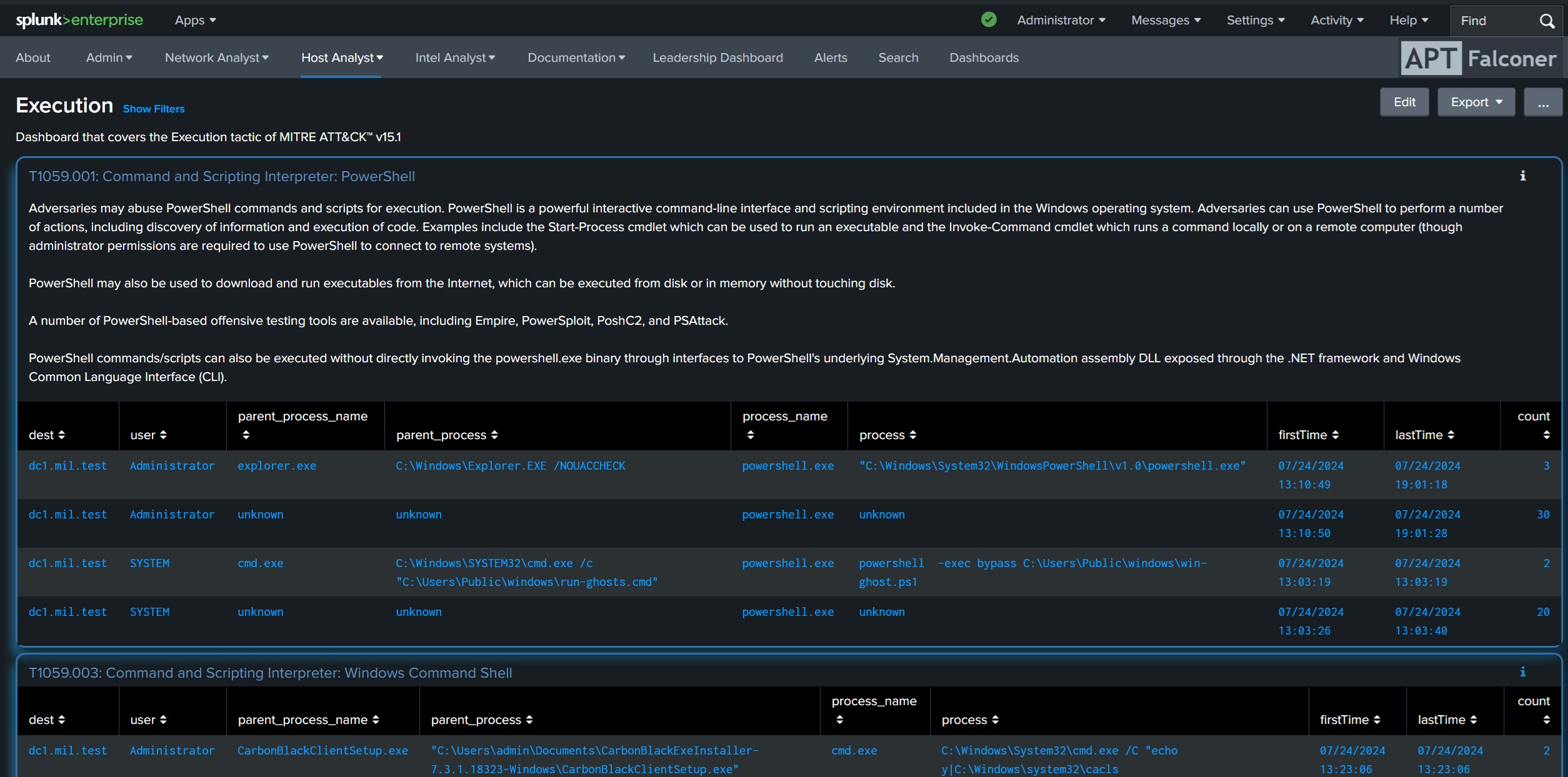
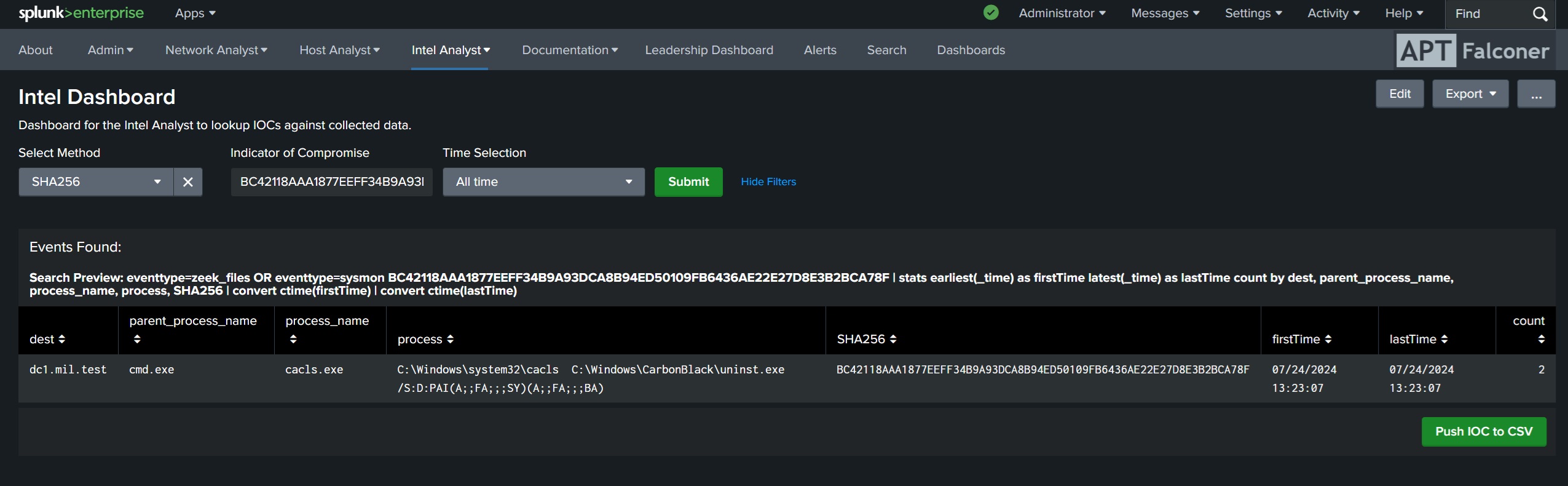
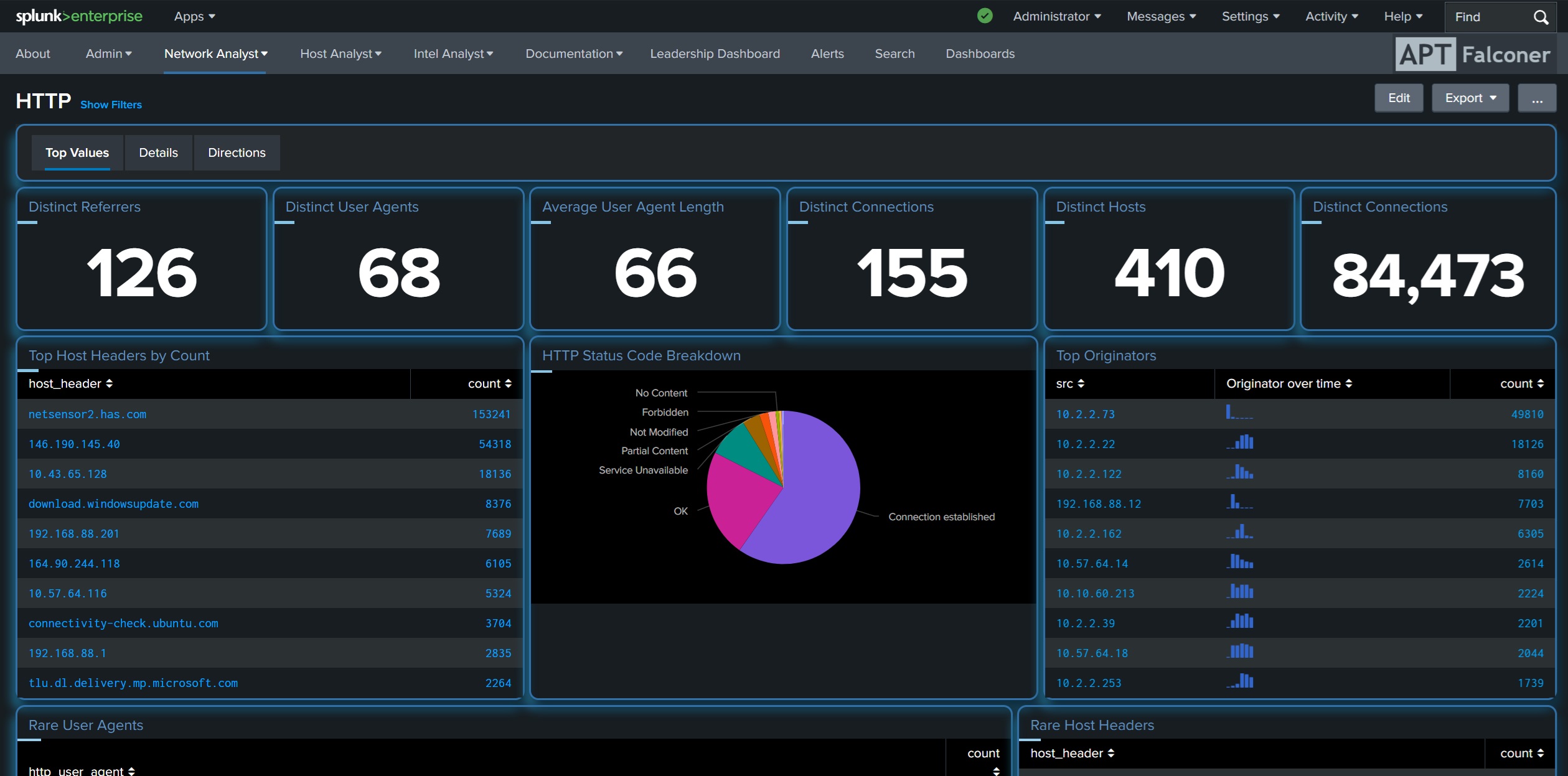
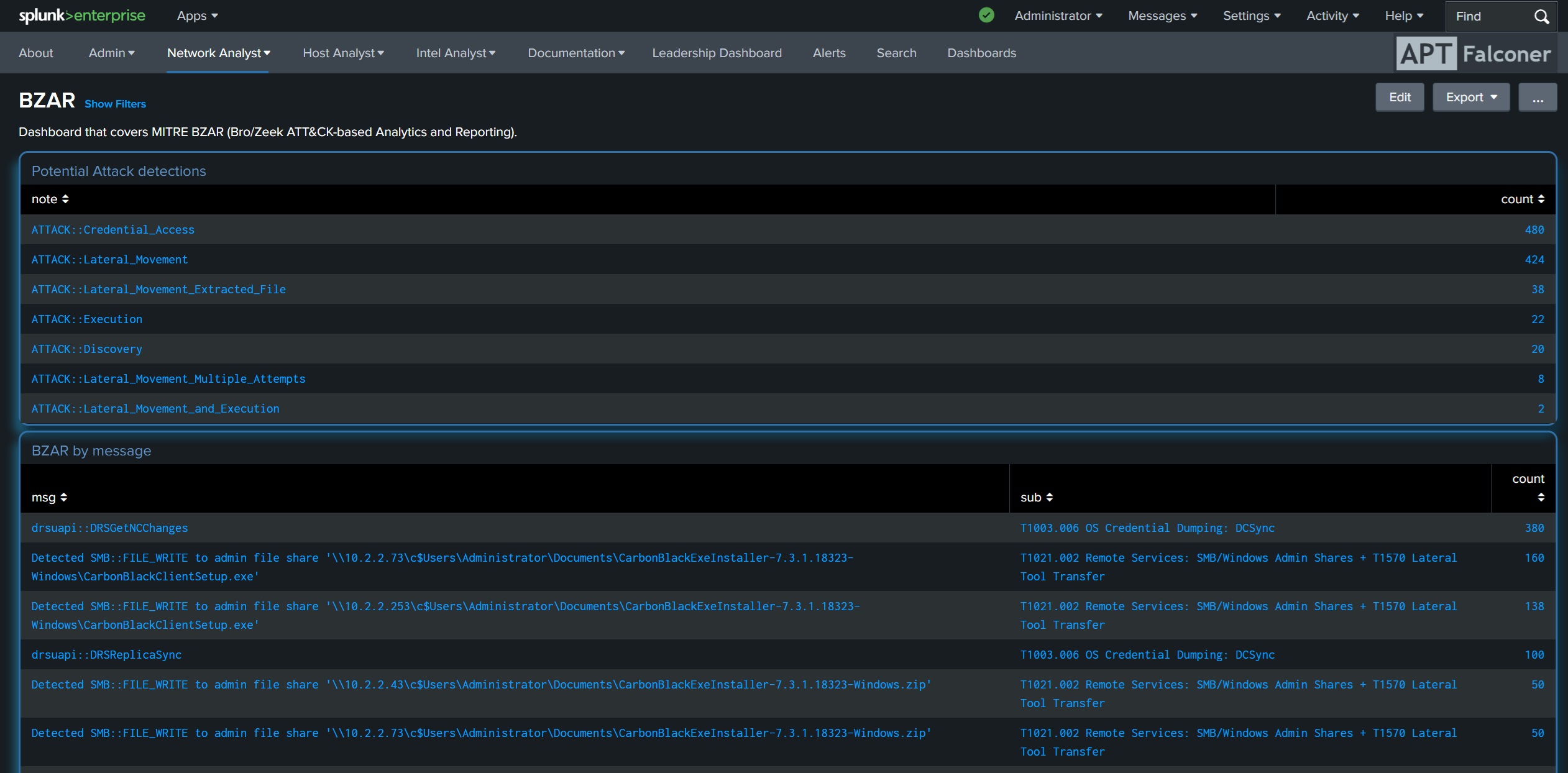










APT Falconer is a threat hunting app built for Splunk, with over 500 pre-built analytics.
Created with Incident Response Teams (IRT) in mind, data feeds are mapped to individual roles.
APT Falconer is easy to configure to work with your current environment. Utilizing the including Splunk Search Macros you simple navigate to Settings > Advanced Search > Search Macros and change the proper macro to mimic your environment.
EX: If your Sysmon index is named my_sysmon_data change the sysmon_index macro to read index=my_sysmon_data
If you would like to contribute to this project please feel free.
Updated for MITRE ATT&CK v15
Improved macro clutter
Simplified view of most dashboards using stats instead of table.
APT Falconer is a threat hunting app built for Splunk, with over 500 pre-built analytics.
Created with Cyber Protection Teams(CPT) in mind, data feeds are mapped to individual roles.
APT Falconer is easy to configure to work with your current environment. Utilizing the including Splunk Search Macros you simple navigate to Settings > Advanced Search > Search Macros and change the proper macro to mimic your environment.
EX: If your Sysmon index is named my_sysmon_data change the sysmon_index macro to read index=my_sysmon_data
If you would like to contribute to this project please feel free.
This app is still in beta, you will find bugs please email bmatlock@splunk.com
As a Splunkbase app developer, you will have access to all Splunk development resources and receive a 10GB license to build an app that will help solve use cases for customers all over the world. Splunkbase has 1000+ apps from Splunk, our partners and our community. Find an app for most any data source and user need, or simply create your own with help from our developer portal.