





Anetac Log Export for Splunk is a Splunk app that provides a macros, a search command, and an alert action for exporting Windows Event Logs to Anetac via S3.
Removed JSON encoding of the results. Instead the addon uploads splunk results file.
Update splunk lib to 2.0.2
Remove _yaml.cpython-37m-x86_64-linux-gnu.so binary file
Updated splunk lib version to 2.0.2
Changes in version 1.0.13
- Files are compressed using GZIP before uploading to S3
- New search macro anetac_windows_auth allows exporting the minimum set of logs
In version 1.0.1 we fixed the following errors and warnings found by app inspect:
- change file permissions under appserver/static/js/build/ to 644
- change dimensions of appLogo_2x.png to 320x80
- remove shortdesc from commands.conf and searchbnd.conf
- specify targetWorkloads in app.manifest
In version 1.0.7 we removed aob_py3 folder, which broke the alert action, because the folder contained Splunk helper dependencies.
In version 1.0.8 we added aob_py3 folder back, but left out the binary Shared Object file. The alert action has been tested to work in version 1.0.8
Anetac Log Export for Splunk is a Splunk add that provides a macros, a search command, and an alert action for exporting Windows Event Logs to Anetac via S3.
Login to your Splunk instance and navigate to Apps > Manage Apps. Click on Install app from file and select the sanetac-log-export-***.tgz file. Click Upload and follow the prompts to install the app.
TBD after the app is published to Splunkbase.
Navigate to the Anetac Log Export app by clicking on Apps > Anetac Log Export. The Configuration tab will be displayed by default.
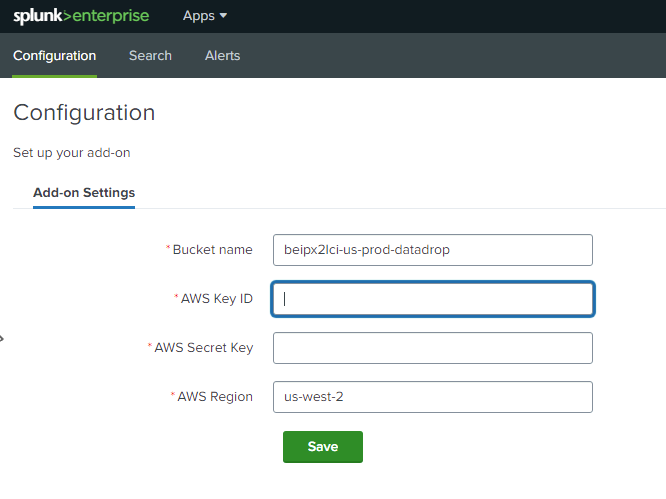
The configuration page contains the following fields:
- Bucket name: The name of the S3 bucket - provided to you by Anetac
- AWS Key ID: The AWS Access Key ID - provided to you by Anetac
- AWS Secret Key: The AWS Secret Access Key - provided to you by Anetac
- AWS Region: The AWS region where the S3 bucket is located - provided to you by Anetac
Make sure to enter configuration details on the Configuration tab before using the app.
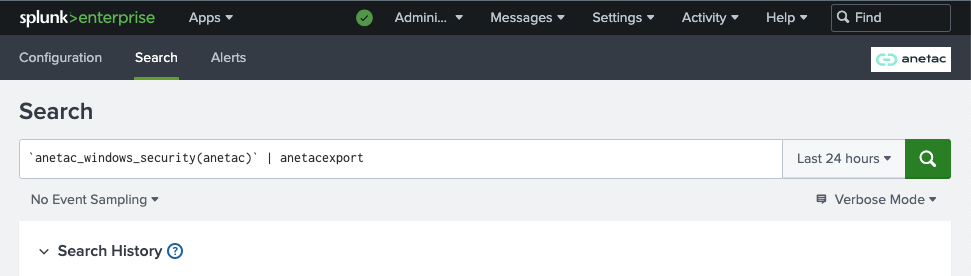
To perform a one time export of Windows Event Logs to Anetac, navigate to the Anetac Log Export app by clicking on Apps > Anetac Log Export. Click on the Search tab and enter the following search query.
Replace INDEX_NAME with the name of the Splunk index that contains Windows Event Logs. Note, that the first part of the command is a Splunk search macros and has to be surrounded by backticks.
`anetac_windows_security(_INDEX_NAME_)` | anetacexport
To set up continuous streaming of Windows Event Logs to Anetac, you need to create an alert in Splunk. First, navigate to the Anetac Log Export app by clicking on Apps > Anetac Log Export. Click on the Search tab and enter the following search query.
Replace INDEX_NAME with the name of the Splunk index that contains Windows Event Logs. Note, that the command is a Splunk search macros and has to be surrounded by backticks.
`anetac_windows_security(_INDEX_NAME_)`
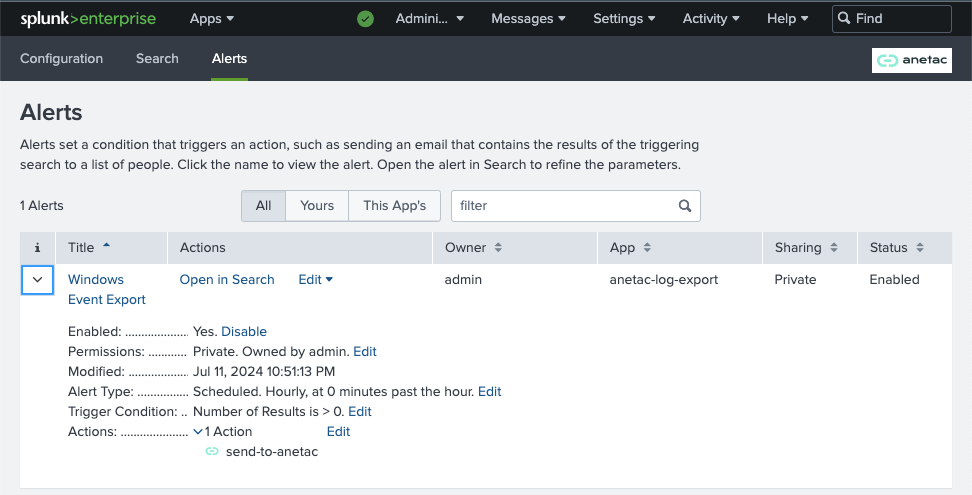
Click on Save As and select Alert. Enter the following details:
- Name: A name for the alert. Enter "Anetac Export"
- Description: A description for the alert. Enter "Export Windows Event Logs to Anetac"
- Alert type: Select Scheduled
- Run every: Select Run every hour
- Trigger Conditions: Select Number of Results and is greater than 0
- Trigger: Select Once
- Alert Actions: Click on Add Actions and select send-to-anetac
Save to save the alert.As a Splunkbase app developer, you will have access to all Splunk development resources and receive a 10GB license to build an app that will help solve use cases for customers all over the world. Splunkbase has 1000+ apps from Splunk, our partners and our community. Find an app for most any data source and user need, or simply create your own with help from our developer portal.