





SIEM: Splunk v. 9.x or higher.
Note: If you have an all-in-one Splunk environment, use this guide to install the app. If you have a distributed Splunk environment, please contact SOC Prime support for help with installation since it may be specific to your configuration.
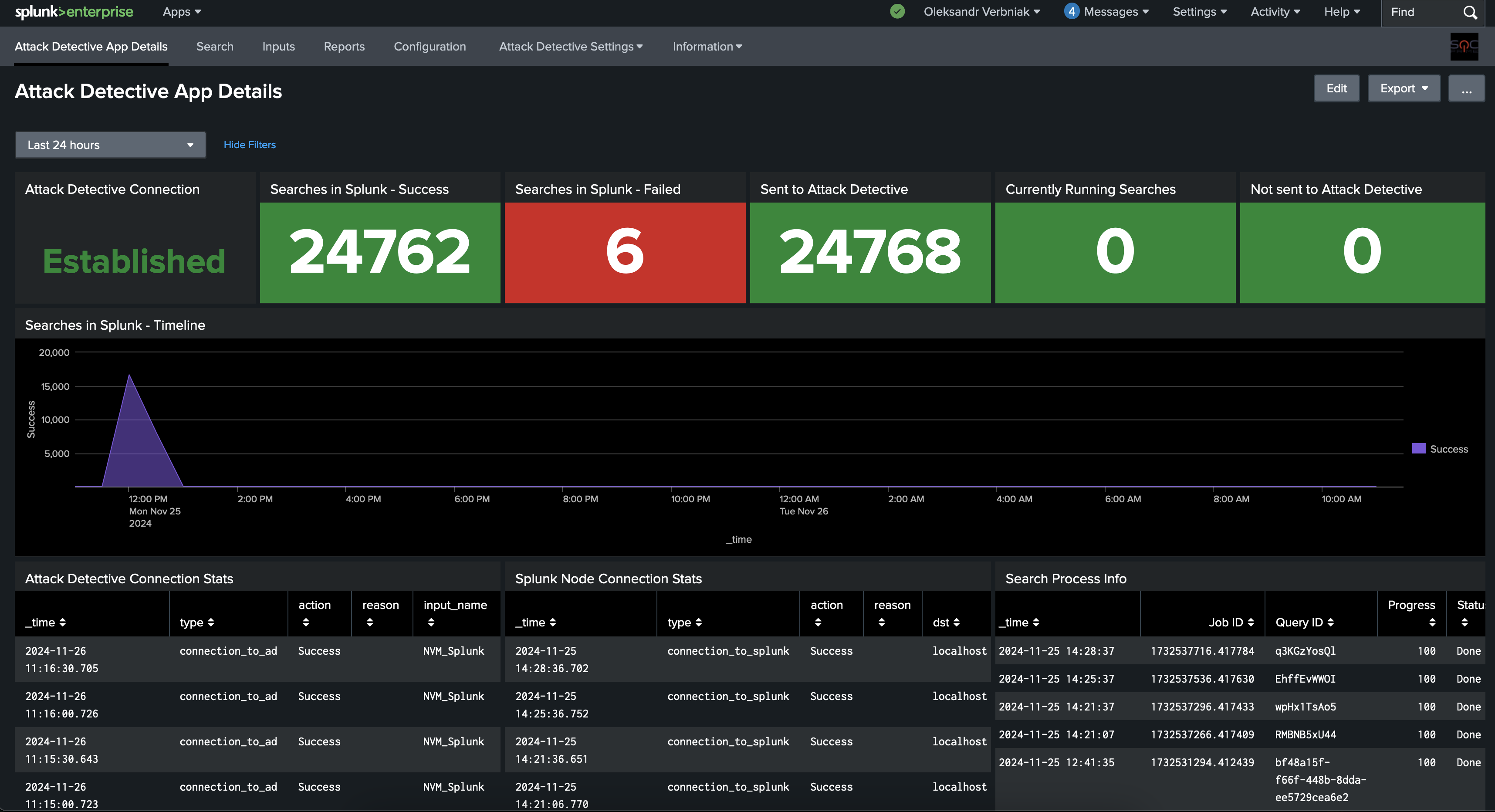
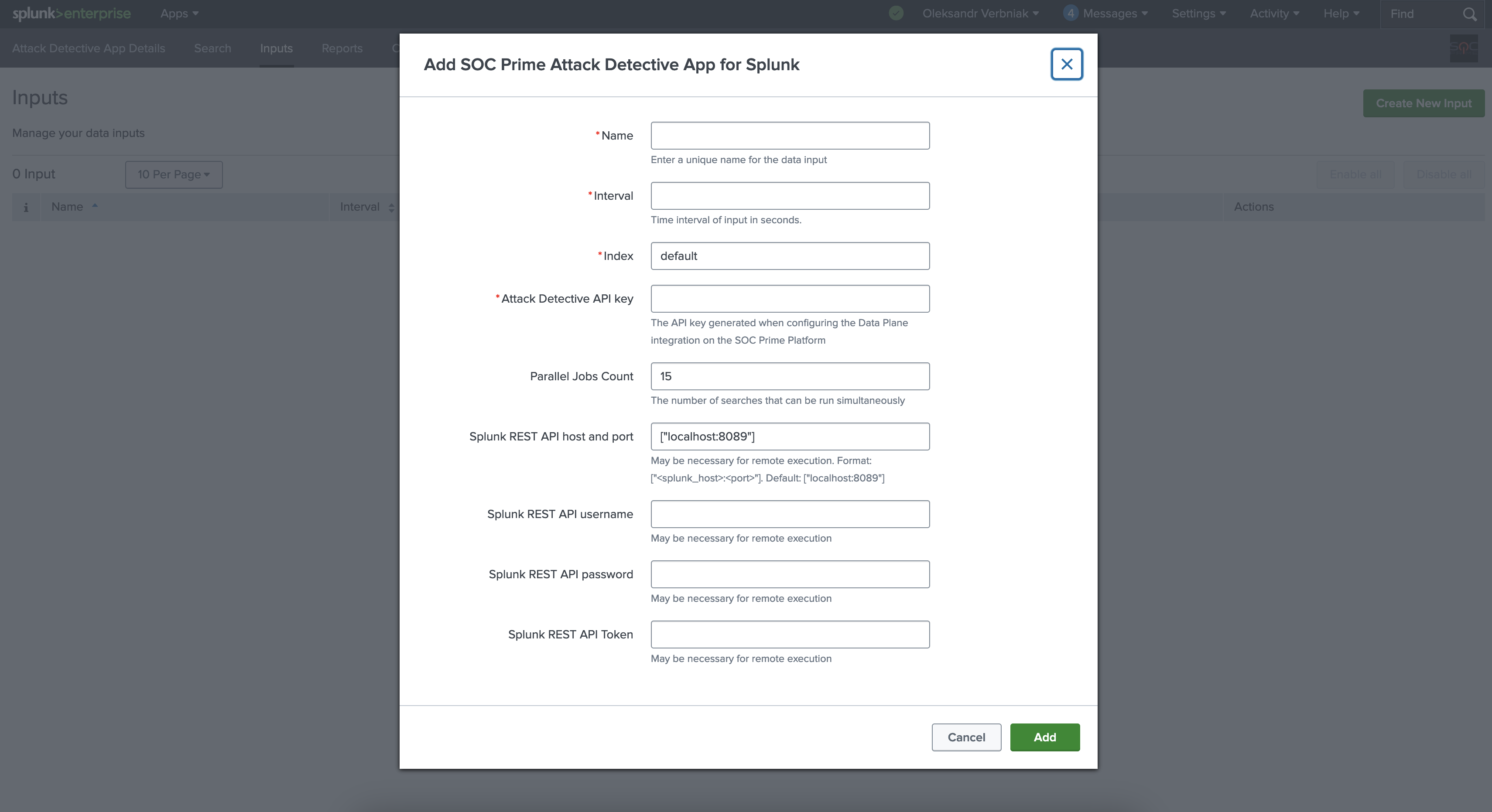
After installation, create an index for the App and configure getting the searches from Attack Detective on the Inputs tab:
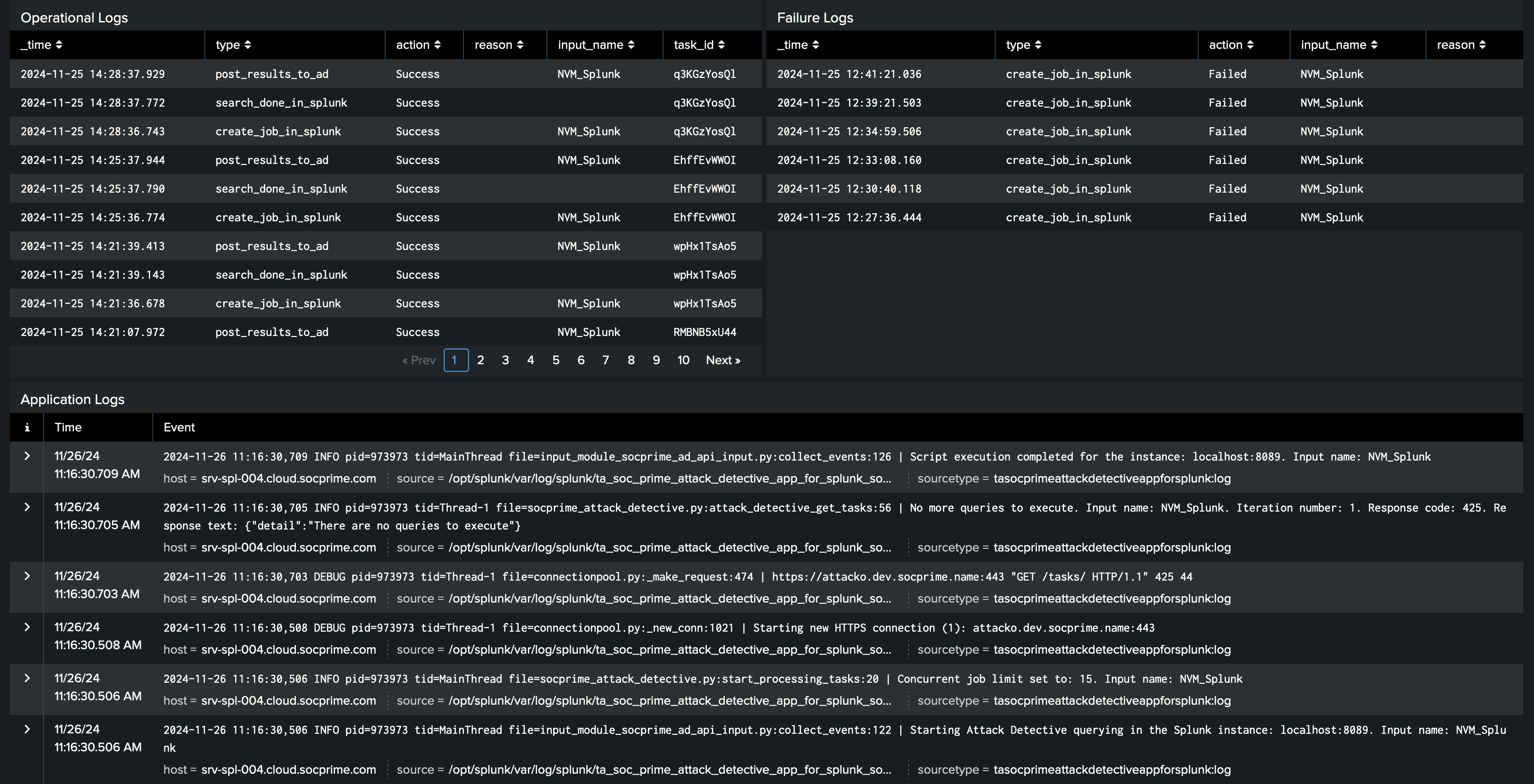
The index created during the configuration is filled by the results of a special search run each hour. This data is used by Attack Detective to speed up data audits and scans. If you're going to run data audits or scans that cover time periods before the app has been installed (like for the last 7 or 30 days), you need to run the Reports search manually at least for the same period, which will generate all audit data historically for each day of the period. To do this:
1. In the App menu, go to Reports.
2. Click Open in Search for SOC Prime Attack Detective Data Audit EventCodes with Indexes - Filling the Trend.
3. Select the same or greater time period as will be used for your data audit or scan in the calendar picker next to the Run button.
4. Run the search.
5. The search can take a long time depending on the selected period. You can send the job to the background. To do this:
5.1 Go to Job > Send Job to Background in the menu under the search query.
5.2 The Send Job to Background window appears. Optionally, you can set the Email when complete checkmark and enter your email to receive an email notification when the job is finished.
5.3 Click the Send to Background button.
6. Wait until the search is finished. After that, the index socprime will be populated with trended historical data, so you can run a Data Audit or Scan for the same period.
Note that the map and collect commands are used during Data Audits, and Splunk potentially can recognize them as risky.
All configurations related to investigations are made in Attack Detective on the SOC Prime Platform. Before installing the SOC Prime Attack Detective App for Splunk, make sure to configure your on-prem Splunk Data Plane on the SOC Prime Platform.
To learn more, see the Attack Detective User Guide (to open the Guide, you need to be logged in to your SOC Prime Platform account).
As a Splunkbase app developer, you will have access to all Splunk development resources and receive a 10GB license to build an app that will help solve use cases for customers all over the world. Splunkbase has 1000+ apps from Splunk, our partners and our community. Find an app for most any data source and user need, or simply create your own with help from our developer portal.