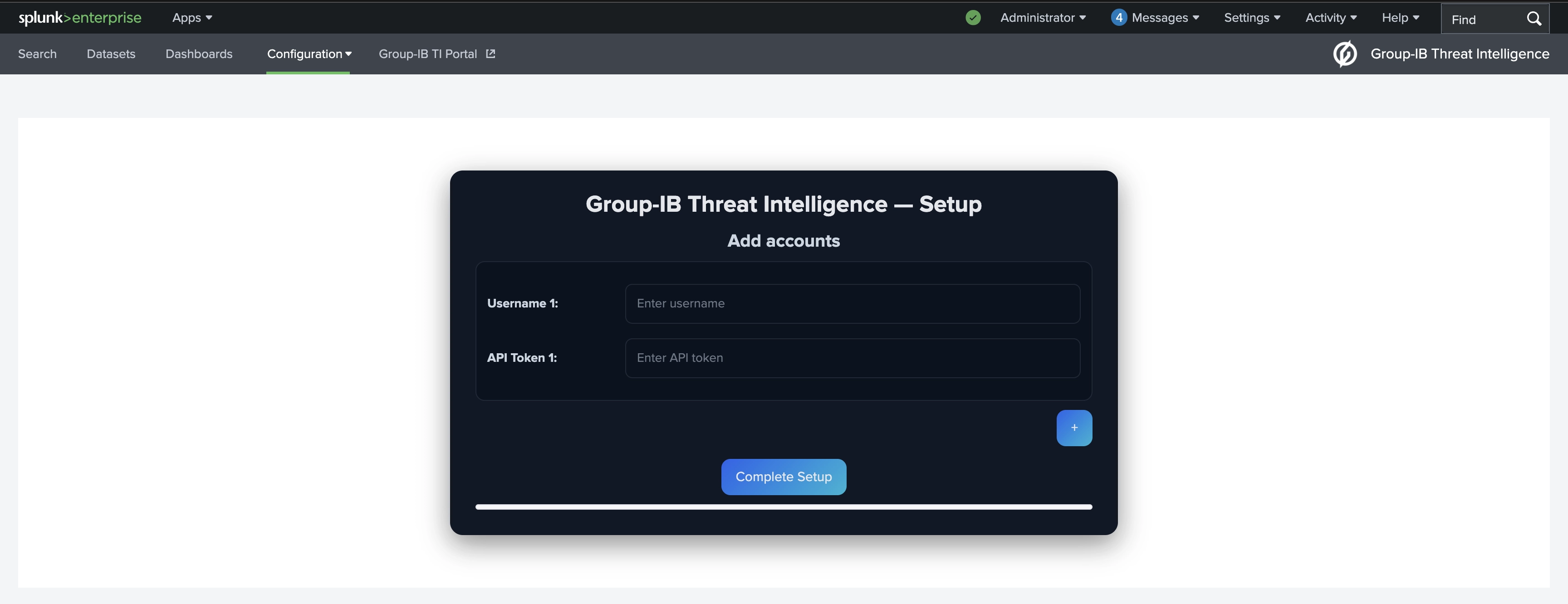








Once the configuration is complete, the following sourcetypes become available in Splunk.
Note: If you’re using a POC or partner license, access to data is limited to 30 days. The recommended date ranges below are guidelines and can be adjusted according to your needs.
Format: YYYY-MM-DD
| Collection | Sourcetype (gib-ti) | Description | Recommended date |
|---|---|---|---|
| APT::Threat Report | gib_ti_apt_threat | Reports on nation-state APTs activities, including associated indicators (IOCs), attack techniques, and MITRE ATT\&CK mappings. | 2-4 years |
| APT::Threat Actor | gib_ti_apt_threat_actor | Profiles of nation-state groups detailing their characteristics, targets, motivations, and techniques. | 2-4 years |
| Attacks::DDoS | gib_ti_attacks_ddos | Data on Distributed Denial of Service (DDoS) attacks, including targeted resources and attack durations. | 5-10 days |
| Attacks::Deface | gib_ti_attacks_deface | Records of defacement attacks, highlighting compromised websites and related actors. | 5-10 days |
| Attacks::Phishing Group | gib_ti_attacks_phishing_group | Information on phishing attacks, including URLs of phishing websites. Note: do not use IPs for detection - it may cause many false positives. Focus only on URLs. | 3-5 days |
| Attacks::Phishing Kit | gib_ti_attacks_phishing_kit | Collections of phishing website templates, scripts, and configurations used by attackers. | 30 days |
| Compromised::Account | gib_ti_compromised_account_group | The collection contains credentials collected from various phishing resources, botnets, C\&C servers, Darkweb, etc., used by hackers. All indicated sources are unique and private. It also includes combolist and corporate accounts. For Public Breaches - please refer to Compromised::Breached DB. | 2-4 years |
| Compromised::Shops | gib_ti_compromised_access | Sales proposals on compromised data on darkweb marketplaces | 2-4 years |
| Compromised::Group Card | gib_ti_compomised_bank_card_group | Information about compromised bank cards, sourced from card shops, forums, and public leaks. | 2 years |
| Compromised::Breached DB | gib_ti_compromised_breached | Information about publicly leaked databases containing credentials and personal data. Note: hunting rules are on by default here | 90 days |
| Compromised::Discord | gib_ti_compromised_discord | Extracted intelligence from Discord channels and servers, mostly discussions. | 30 days |
| Compromised::Masked Card | gib_ti_compomised_masked_card | Information on compromised masked bank cards gathered from illicit marketplaces and forums. | 90 days |
| Compromised::Messenger | gib_ti_compromised_messenger | Intelligence collected from Telegram channels, including credentials, targeted companies and attack discussions. | 30 days |
| Compromised::Darkweb | gib_ti_compromised_reaper | Intelligence from closed darkweb forums used by threat actors for attack planning and coordination. | 30 days |
| Compromised::SPD | gib_ti_compromised_spd | Data on suspicious payment details (SPD) - bank accounts, crypto wallets, phone numbers and other data used for laundering/illicit/stolen funds | 90 days |
| Cybercriminals::Threat Report | gib_ti_hi_threat | Finance motivated cybercriminals reports, including associated indicators (IOCs), attack techniques, and MITRE ATT\&CK mappings. | 2-4 years |
| Cybercriminals::Threat Actor | gib_ti_hi_threat_actor | Profiles of financially motivated cybercriminals detailing their characteristics, targets, motivations, and techniques. | 2-4 years |
| IOC::Common | gib_ti_ioc_common | General indicators of Compromise (IoCs) from threat reports (cybercriminals and APT) and Malware sections. Consists of Hashes (MD5, SHA1, SHA256), IPs, domains and URLs. Major source of IOCs | 90 days |
| Malware::C\&C | gib_ti_malware_cnc | Information on malware Command-and-Control (C\&C) servers used for data exfiltration and command distribution. This feed is also part of IOC Common | 90 days |
| Malware::Config | gib_ti_malware_config | Extracted malware configuration data. | 90 days |
| Malware::Report | gib_ti_malware_malware | Detailed malware descriptions. | 2-4 years |
| Malware::Signature | gib_ti_malware_signature | Suricata signatures for malware detection. | 30 days |
| Malware::YARA | gib_ti_malware_yara | YARA rules for identifying specific malware families. | 30 days |
| OSI::Git repository | gib_ti_osi_git_repository | Publicly available code from repositories like GitHub, filtered by your hunting rules. Note: hunting rules are on by default here | 30 days |
| OSI::Public Leak | gib_ti_osi_public_leak | Public data leaks from sources like Pastebin, ghostbin, and others., including credentials, database dumps, configuration files, and logs. Note: hunting rules are on by default here | 15 days |
| OSI::Vulnerability | gib_ti_osi_vulnerability | Information on software vulnerabilities, associated exploits, and available proof-of-concept details. | 90 days |
| Suspicious IP::Tor Node | gib_ti_suspicious_ip_tor_nodes | Data about known Tor exit nodes used as anonymity relays. | 5 days |
| Suspicious IP::Open Proxy | gib_ti_suspicious_ip_open_proxy | Information on publicly available proxy servers, including potentially misconfigured proxies. | 5 days |
| Suspicious IP::Scanner | gib_ti_suspicious_ip_scanner | IP addresses identified as scanning or probing corporate networks. | 5 days |
| Suspicious IP::Socks Proxy | gib_ti_suspicious_ip_socks_proxy | IP addresses of infected hosts configured as SOCKS proxies used for anonymized attacks. | 5 days |
| Suspicious IP::VPN | gib_ti_suspicious_ip_vpn | Information about public and private VPN servers identified as potentially malicious or suspicious. | 5 days |
How to use Group-IB collections based on your detection and attribution needs:
IOC::Common collection to trigger SOC alerts based on critical IOCs like hashes, domains, IPs, and URLs. Compromised::Access or Compromised::Messenger collections. Enrich transaction monitoring or IAM tools with compromised cards and retail accounts from Compromised::Masked Card, Group_Card, and SPD.
Intelligence collection: Archive TI data within your Splunk environment for long-term visibility, avoiding full dependency on the Group-IB portal.
Compromised::SPD entries. gibsearch command to pivot on a specific IOC (e.g., domain, IP, hash) and retrieve linked indicators across all Group-IB collections in real time. This is especially useful for investigating suspicious alerts, understanding attacker infrastructure, and expanding threat context.Note: The final workflow depends on you and your preferences. Any scenario must be adapted to suit your infrastructure.
To query Group-IB data inside Splunk, use the following command (change “gib_tia” if you use multiple API accounts):
index="gib_tia" sourcetype="enter the source type you need"
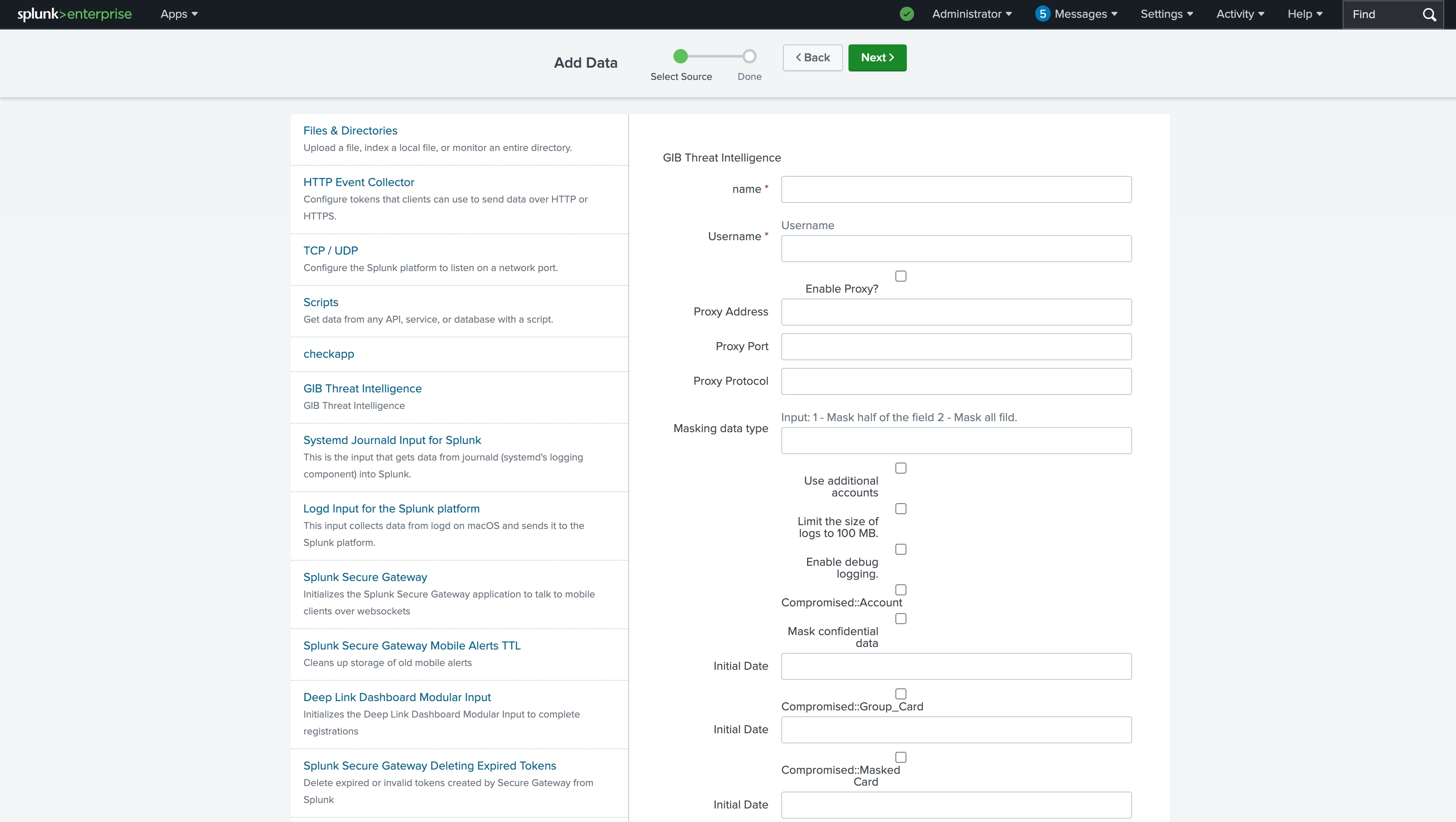
ATTENTION!: Before searching, make sure the relevant collection is enabled in the “Data inputs” of your Splunk or Splunk Heavy Forwarder instance.
For global search use command:
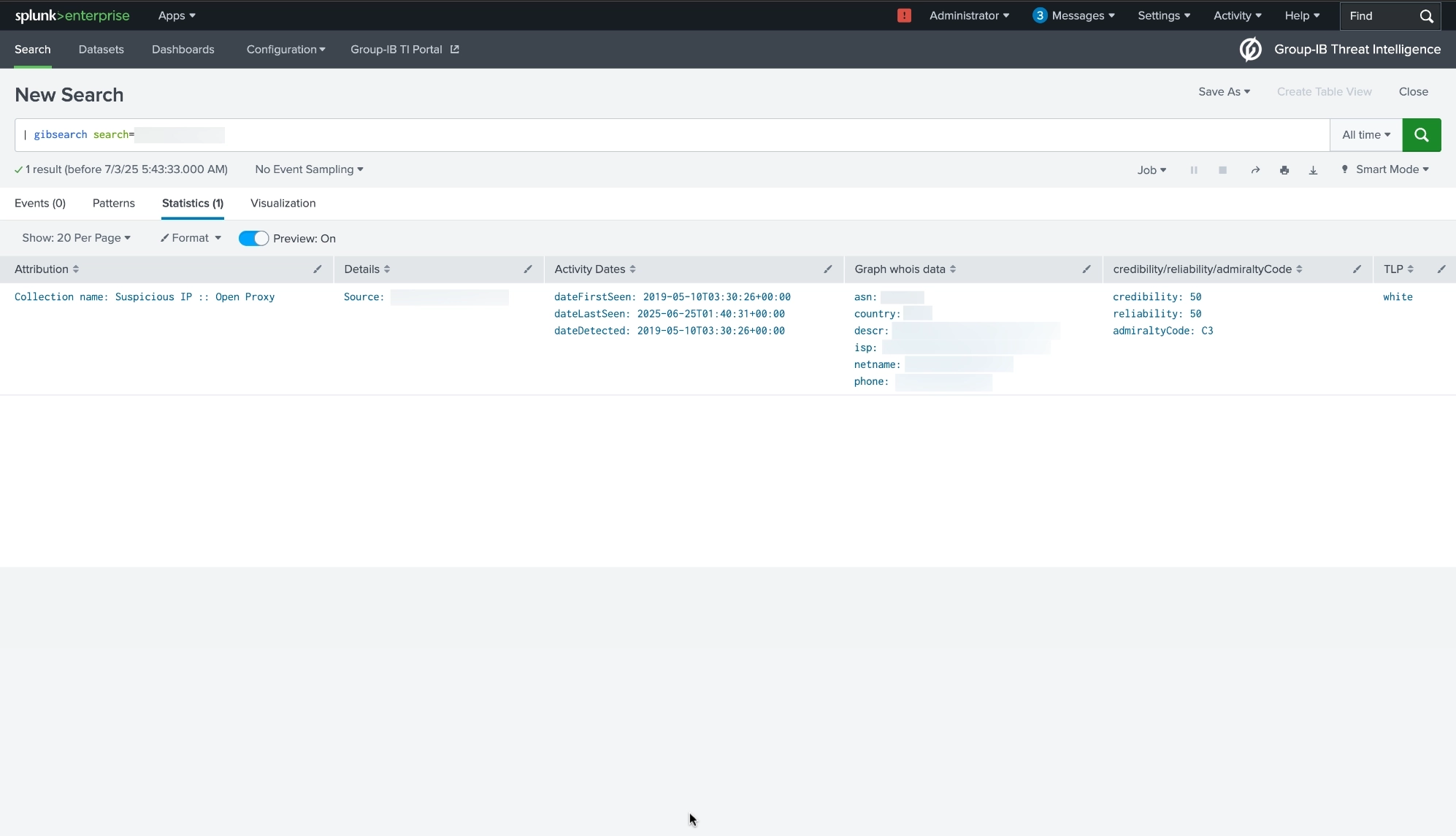
| gibsearch search=<value> username=<value>
NOTE: In Global search ip, domain, hash, url data can be used in the request body. If no username is specified when using multiple accounts, the most recently configured account will be used.
This command provides the opportunity to find references of the desired data in all collections throughout the Group-IB Threat Intelligence system and returns IOCs associated with this data (Date, ID, Hash, CNC, Domain, URL, IP). This search command shows data directly from Group-IB cloud - not your instance data.
Example usage:
| gibsearch search=group-ib.com
As a Splunkbase app developer, you will have access to all Splunk development resources and receive a 10GB license to build an app that will help solve use cases for customers all over the world. Splunkbase has 1000+ apps from Splunk, our partners and our community. Find an app for most any data source and user need, or simply create your own with help from our developer portal.