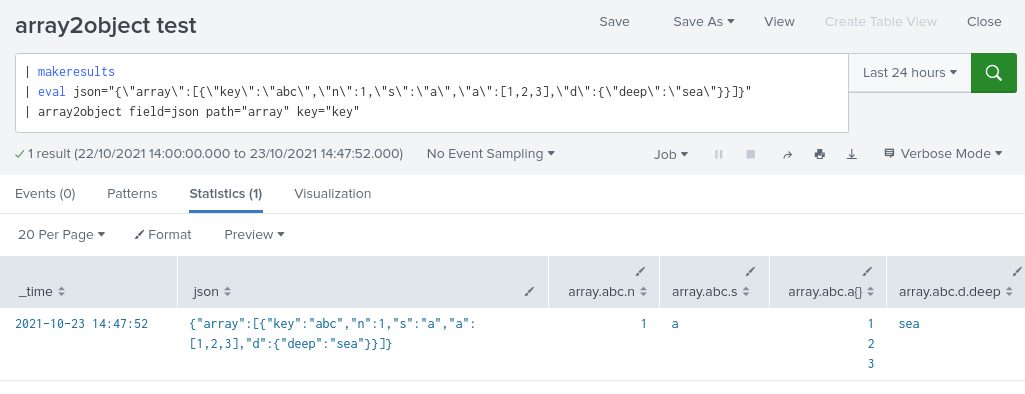
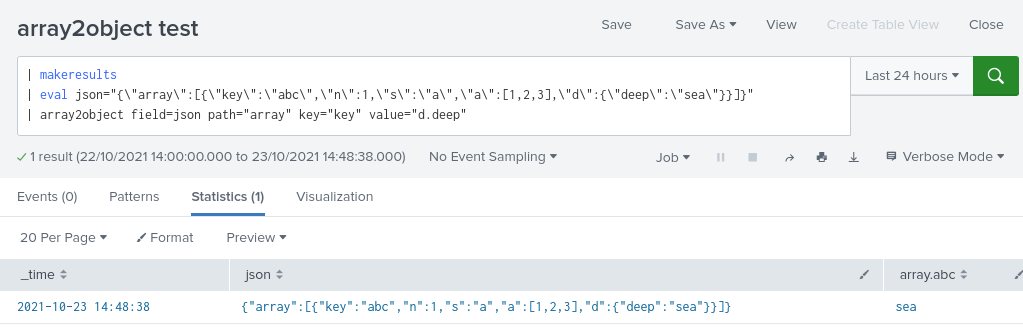




| array2object field=_raw path="<path>" key="<relative path>" value="<relative path>"
Paths are expressed in dot notation, including when entering arrays. For example, event[0].key needs to be written as event.0.key.
Optional, defaults to _raw
Splunk field containing the JSON data to parse.
Mandatory
The path from the root of the JSON object to the array. Must point to an array, and must be written in dot notation eg event.AuditKeyValues.
Mandatory
The relative path from the array, to the value which will be used as the key for each array item. Ideally the value of this field would be unique but the command will create multivalue fields if there is overlap.
Optional, defaults to all children except the key
The relative path from the array, to the value(s) of the new field. Typically used to set the output to a single value like "ValueString", but accepts a relative path, and all children from the path will be added.
CrowdStrike's EventStream data contains an array of objects called AuditKeyValues, where each member contains a object with the keys "Key" and "ValueString". From the root of the JSON object, this arrays path would be "event.AuditKeyValues" in dot notation.
"event":{
"AuditKeyValues":[
{"Key":"actor_cid","ValueString":"abcdef1234567890"},
{"Key":"target_user","ValueString":"brett.whynot@gmail.com"}
]
}
Using the array2object command will create new fields using the value of the key for each of the arrays objects:
| array2object path="event.AuditKeyValues" key="Key"
event.AuditKeyValues.actor_cid.ValueString = "abcdef1234567890"
event.AuditKeyValues.target_user.ValueString = "brett.whynot@gmail.com"
When there is only a single value expected (key value pairs), you can specify the value path to get shorter field names:
| array2object path="event.AuditKeyValues" key="Key" value="ValueString"
event.AuditKeyValues.actor_cid = "abcdef1234567890"
event.AuditKeyValues.target_user = "brett.whynot@gmail.com"
Updated Splunklib and metadata.
Reimplement lib directory and added distsearch.conf to fix use in distributed search.
Moved lib directory into bin directory, as lib is not included in bundle replication. All versions prior to 1.0.0 will need to be installed on search peers to function.
Updated splunklib to 1.6.18
Bugfix when key field was missing. Updated fixes to Splunklib.
Add support for dot paths to the key field too.
Major bug fix related to dynamic fields and Splunklib
https://github.com/splunk/splunk-sdk-python/issues/401
As a Splunkbase app developer, you will have access to all Splunk development resources and receive a 10GB license to build an app that will help solve use cases for customers all over the world. Splunkbase has 1000+ apps from Splunk, our partners and our community. Find an app for most any data source and user need, or simply create your own with help from our developer portal.