










The Fortinet FortiWeb App for Splunk provides real-time and historical dashboard and analytical reports on threats, traffic, events for all products across the FortiWeb physical and virtual appliances. The integrated solution pinpoints threats and attacks with faster response times without long exposure in unknown troubleshooting state.
With the massive set of logs and big data aggregation through Splunk, the Fortinet FortiWeb App for Splunk is certified with pre-defined threat monitoring and performance indicators that guide network security practices a lot easier in the datacenter. As the de facto trending dashboard for many enterprises or service providers, IT administrators can also modify the regular expression query to custom fit for advanced security reporting and compliance mandates.
Make sure Fortinet FortiWeb Add-On for Splunk has been installed and configed before you proceed.
The compatible FortiWeb version is 6.2.0 and later.
There are three ways to install the add-on:
Install from Splunk web UI: Manage Apps->Browse more apps->Search keyword "Fortiweb" and find the add-on with Fortinet logo->Click "Install free" button->Click restart splunk service.
Install from file on Splunk web UI: Manage Apps->Install from file->Upload the .tgz file which is downloaded from https://splunkbase.splunk.com/app/4679 ->check the upgrade box-> click restart splunk service.
Install from file on Splunk server CLI interface: Extract the .tgz file->Place the SplunkAddOnForFortiWeb folder under $SPLUNK_HOME/etc/apps-> Restart Splunk service.
There are three ways to install the app:
Install from Splunk web UI: Manage Apps > Browse more apps > Search keyword "Fortiweb" > Click "Install free" button > Click Restart Splunk Service.
Install from file on Splunk web UI: Manage Apps > Install from file > Upload the .tgz file which is downloaded from https://splunkbase.splunk.com/app/4680 > Click Restart Splunk service.
Install from file on Splunk server CLI interface: Extract the .tgz file->Place the SplunkAppForFortiweb folder under $SPLUNK_HOME/etc/apps > Restart Splunk Service.
Through Splunk Web UI:
Settings -> Data Input -> UDP -> New Local UDP
Port: 514 (Example, can be modified according to your own plan)
leave other parameters as is.
Note: the UDP port, 514 in this example should be opened in firewall for logs to pass through.
Press the button "Next".
Source Type: "Select"
Click on the "Select Source Type" Drop Menu, input "fwb" in the filter, press Enter, and select the item "fwb_log".
Fortinet FortiWeb Add-On for Splunk will by default automatically extract FortiWeb log data from inputs with sourcetype "fwb_log".
leave other parameters as is.
Press the button "Review".
Make sure everything is correct and press the button "Submit".
We could either enable data model acceleration on Splunk GUI Settings->Data Models->FortiWeb FOS Log.
Or on Splunk search head, where the app is installed, create "local" folder under $SPLUNK_HOME/etc/apps/SplunkAppForFortiWeb/ and create a file in this "local" folder named datamodels.conf with the following content:
[fwb_fos]
acceleration = 1
acceleration.earliest_time = -1mon
Then restart Splunk service.
config log syslog-policy
edit splunk
config syslog-server-list
edit 1
set server x.x.x.x
set port 514 (Example. Should be the same as in data input of Splunk server)
end
end
config log syslogd
set policy splunk
set status enable
end
Through Splunk Web UI:
Apps -> Search & Reporting
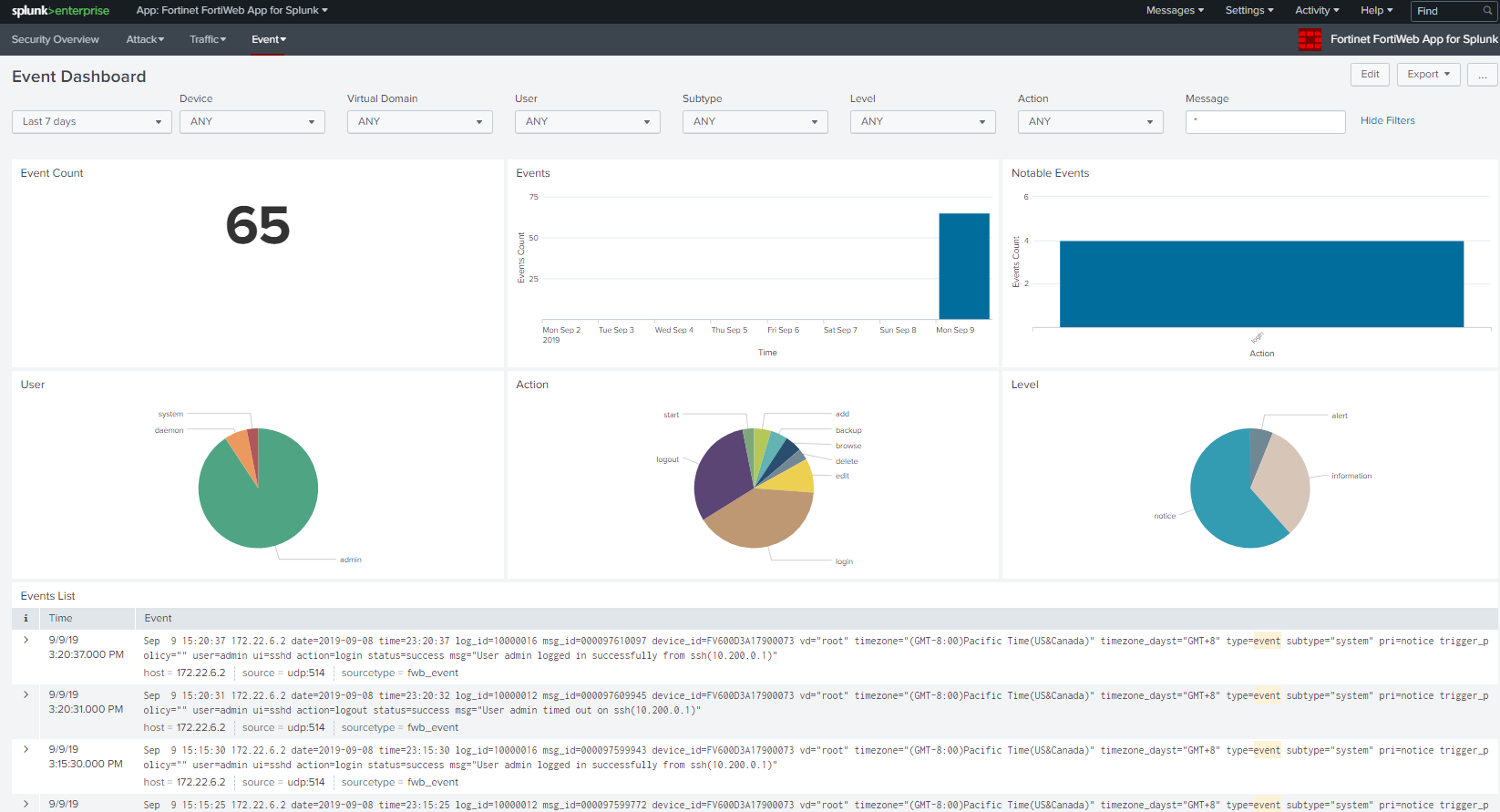
If attack logs have been sent to Splunk, input 'sourcetype="fwb_attack"' in the search window, change the time range if needed.
Then the attack logs will be listed below.
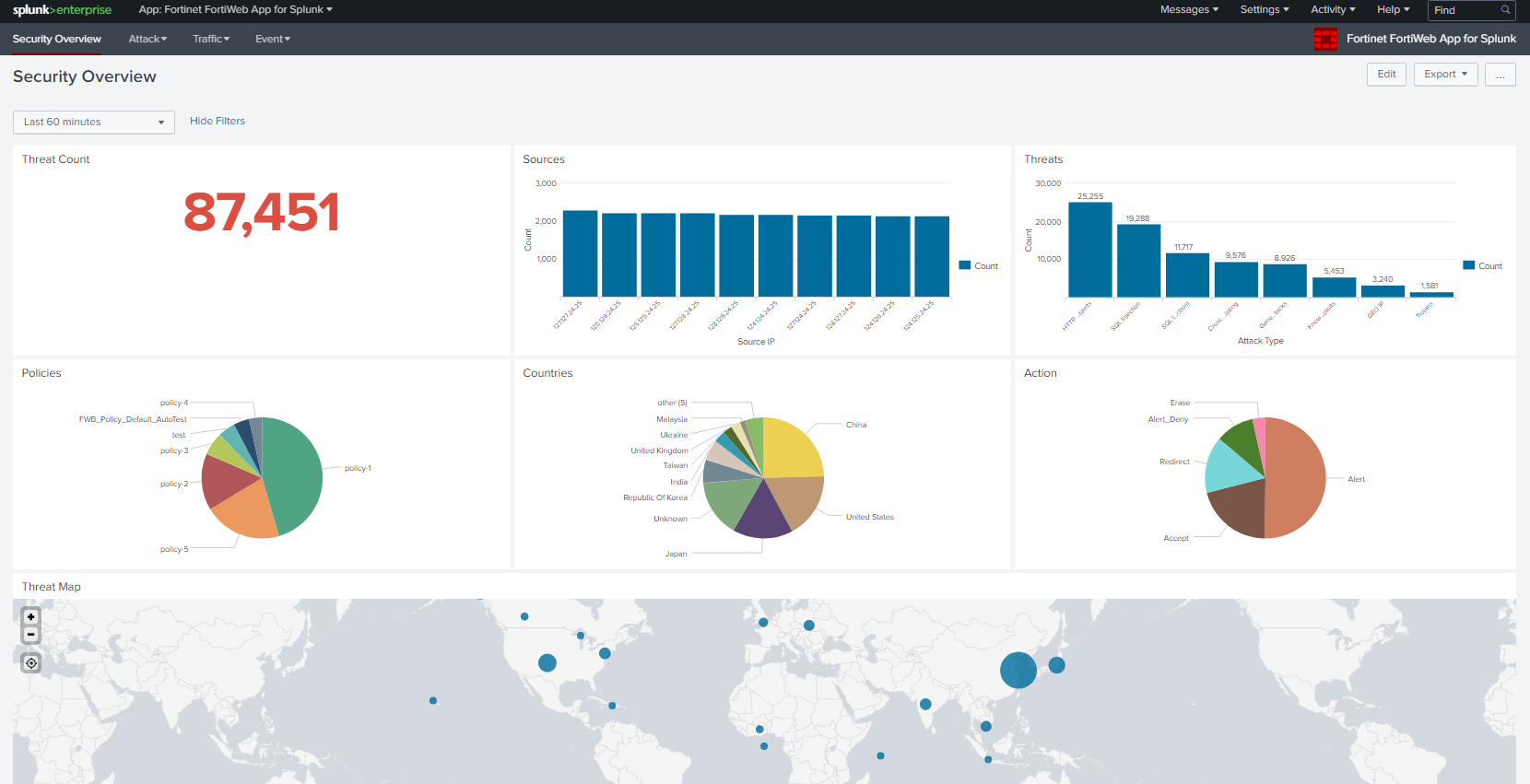
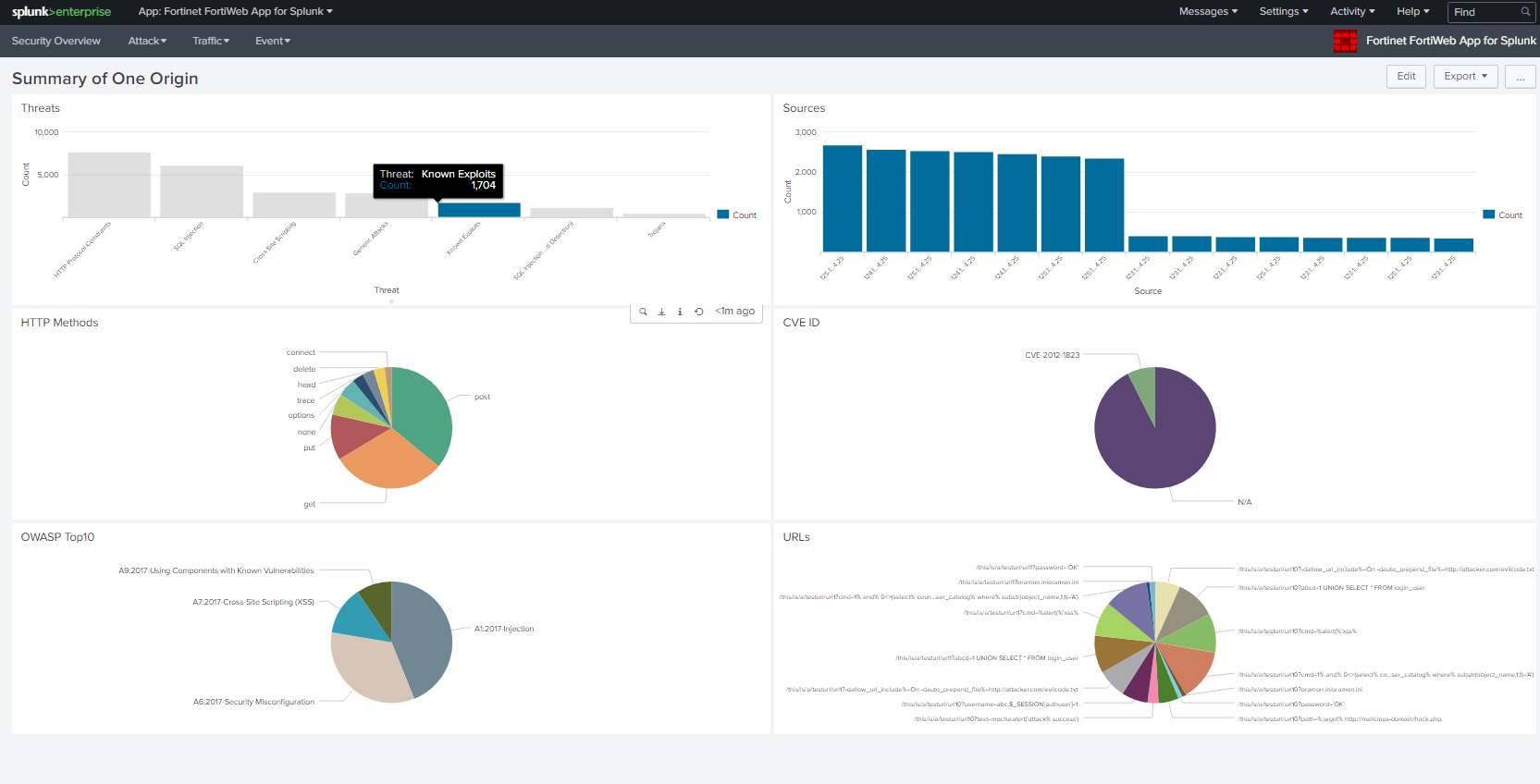
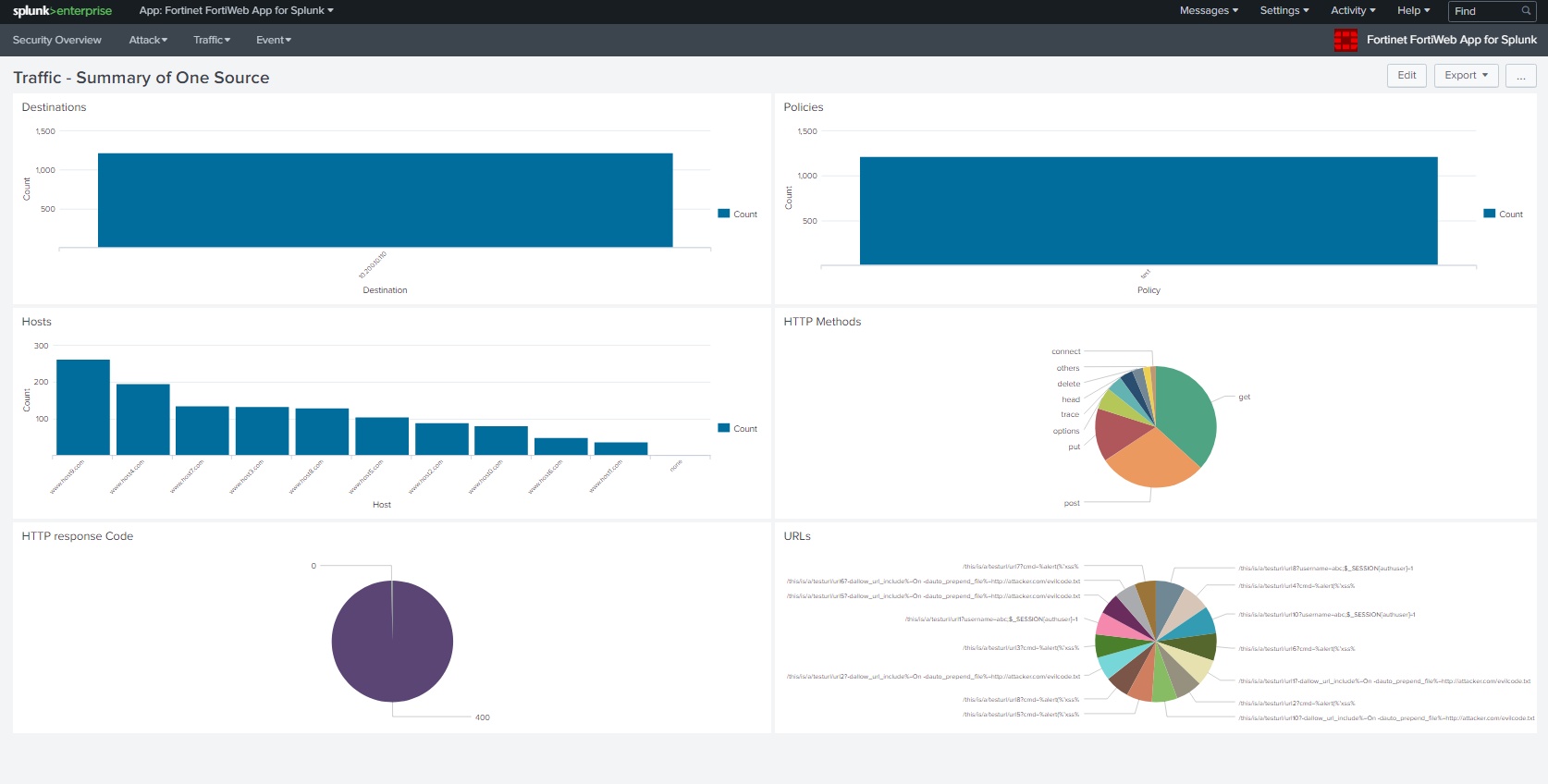
At this point, you will see data parsed and presented on the dashboard of Fortinet FortiWeb App for Splunk.

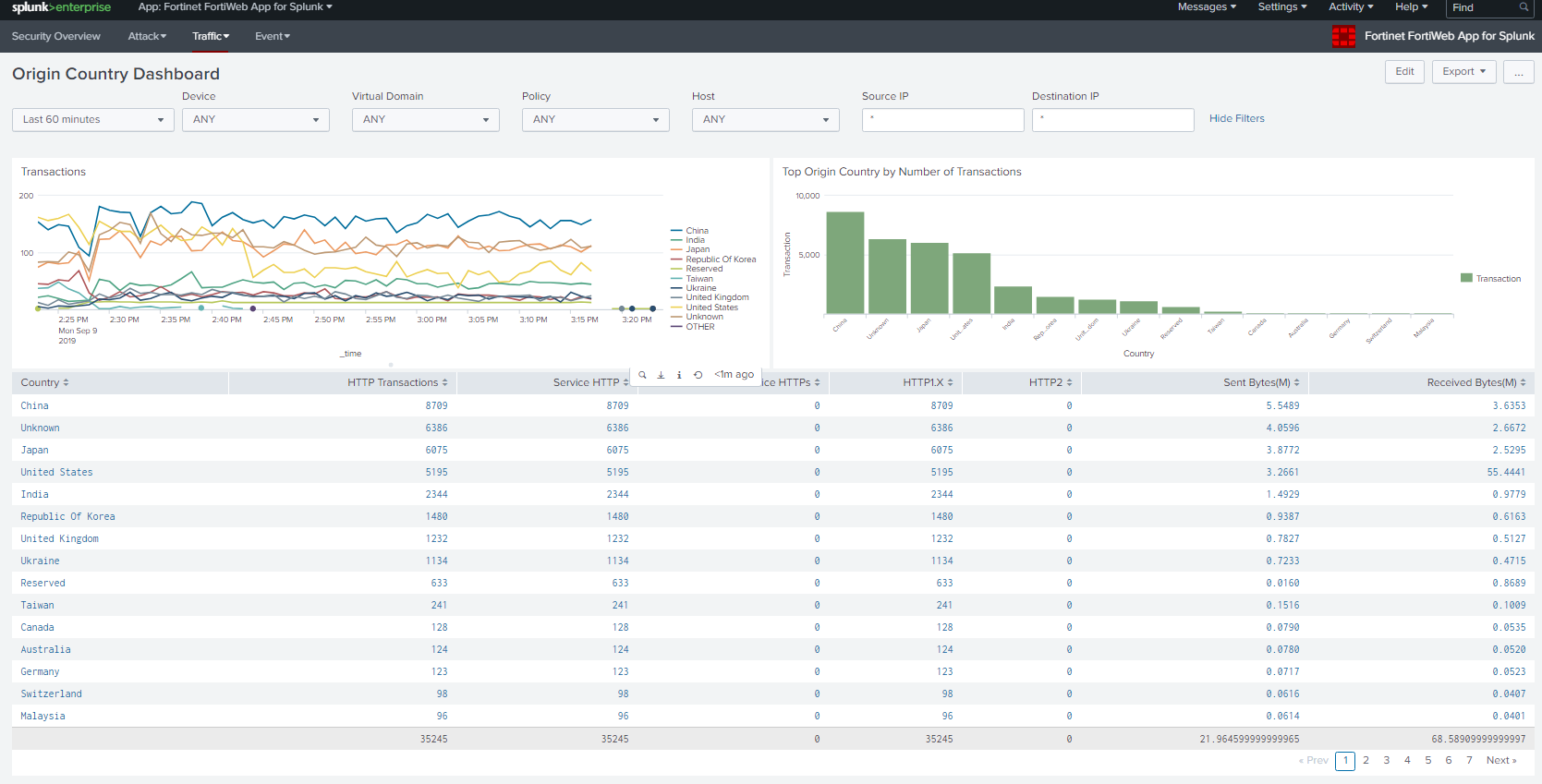

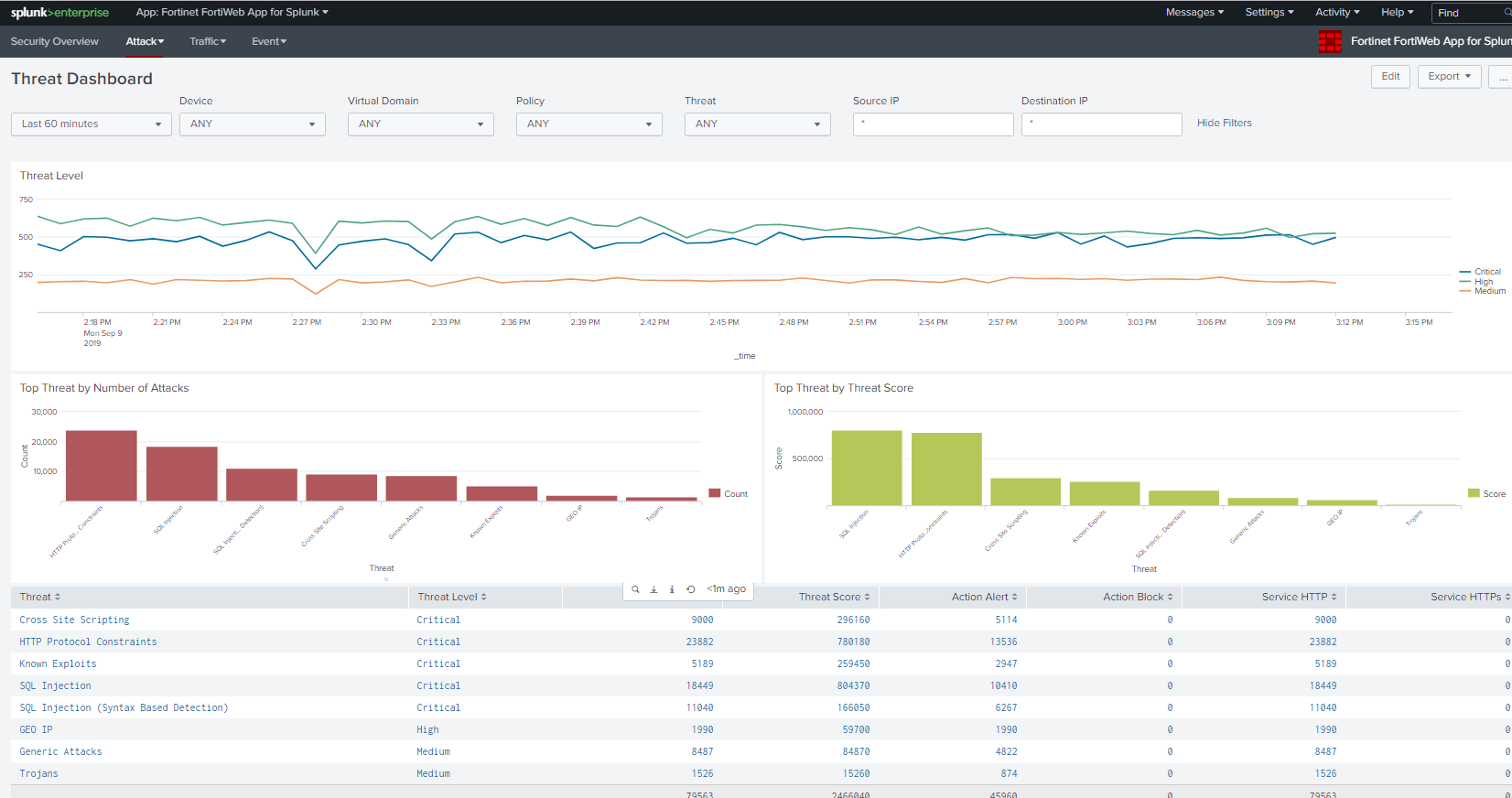
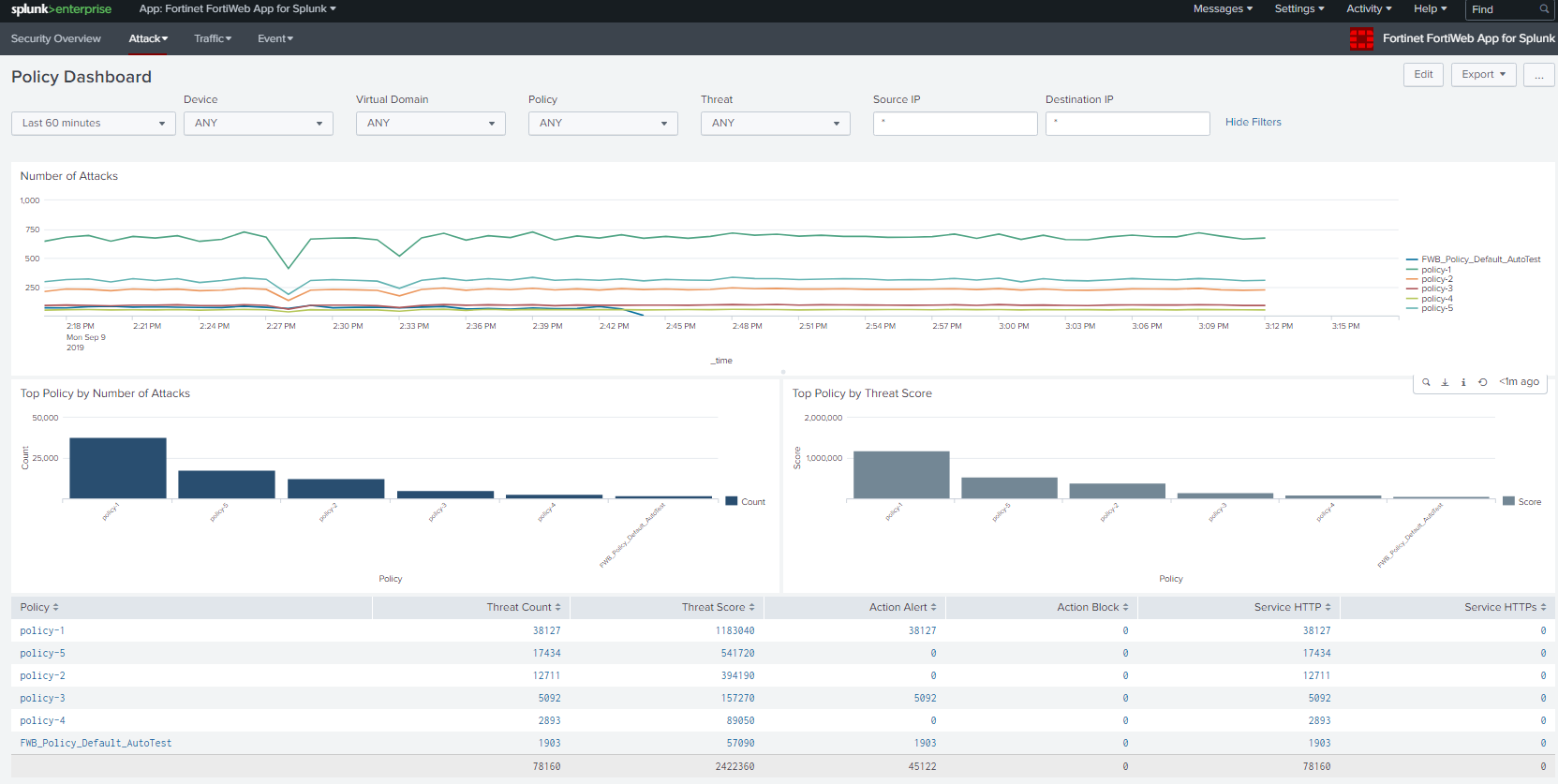
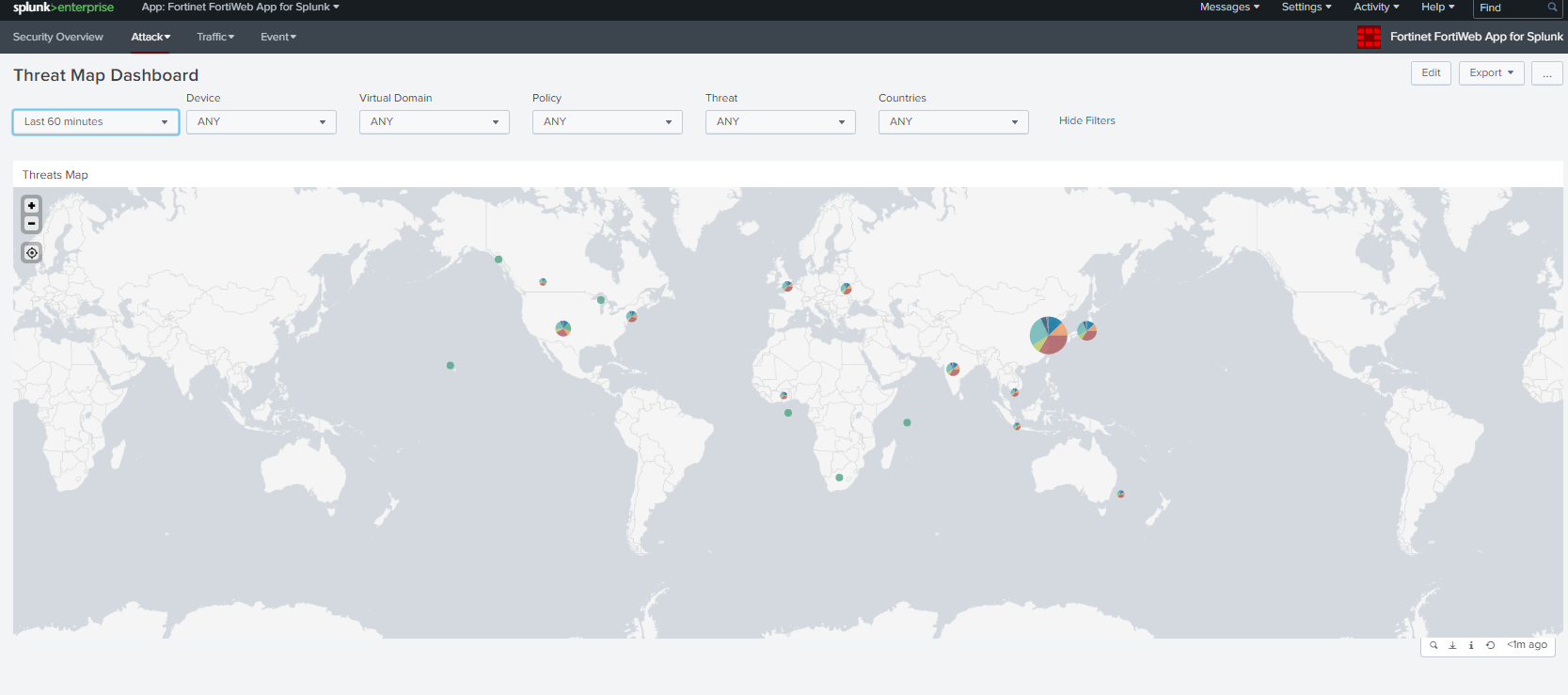

For more information on the App support, email splunk_app@fortinet.com for further support.
As a Splunkbase app developer, you will have access to all Splunk development resources and receive a 10GB license to build an app that will help solve use cases for customers all over the world. Splunkbase has 1000+ apps from Splunk, our partners and our community. Find an app for most any data source and user need, or simply create your own with help from our developer portal.