



Table of Contents
Overview
Installation and Configuration
Overview
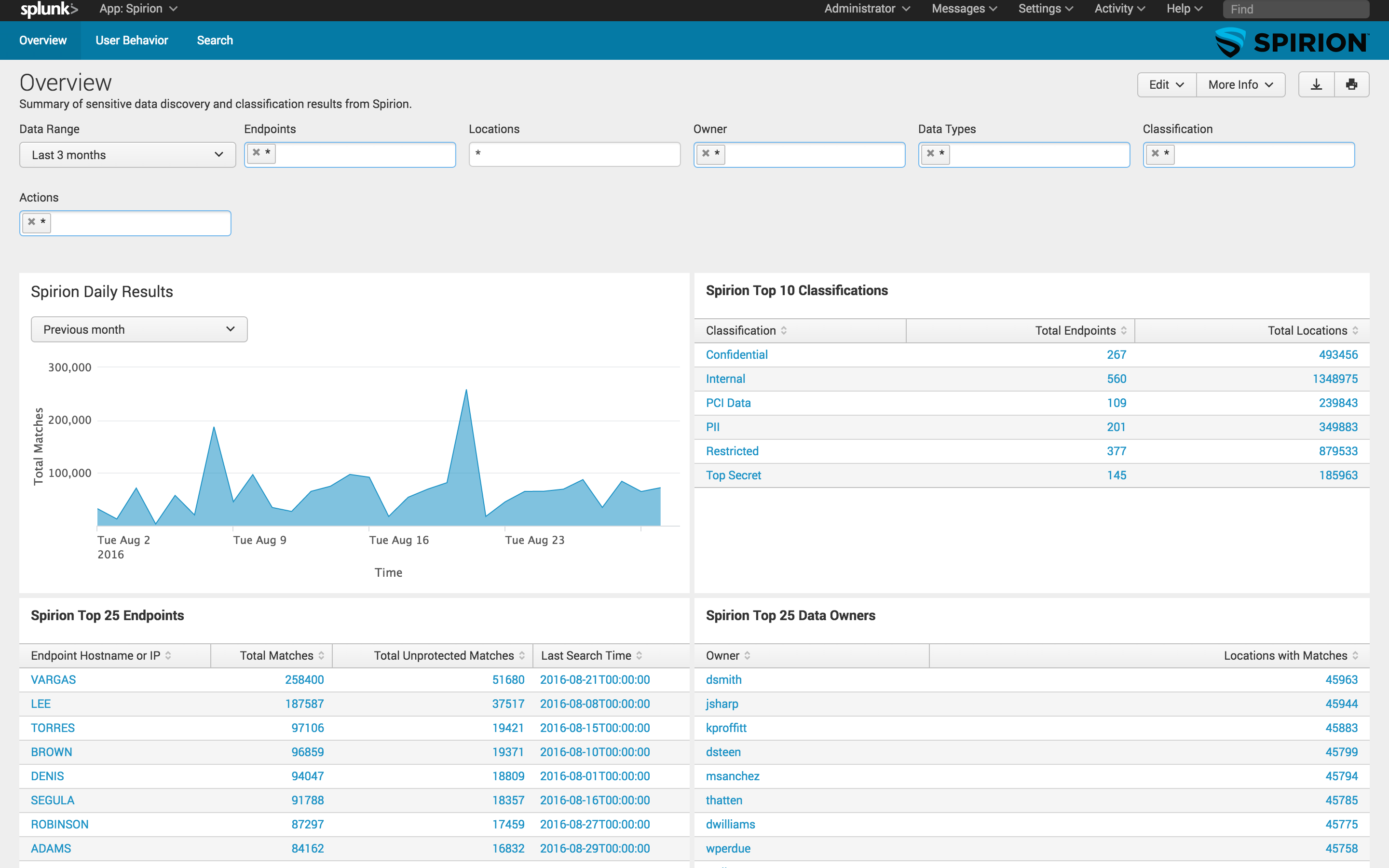
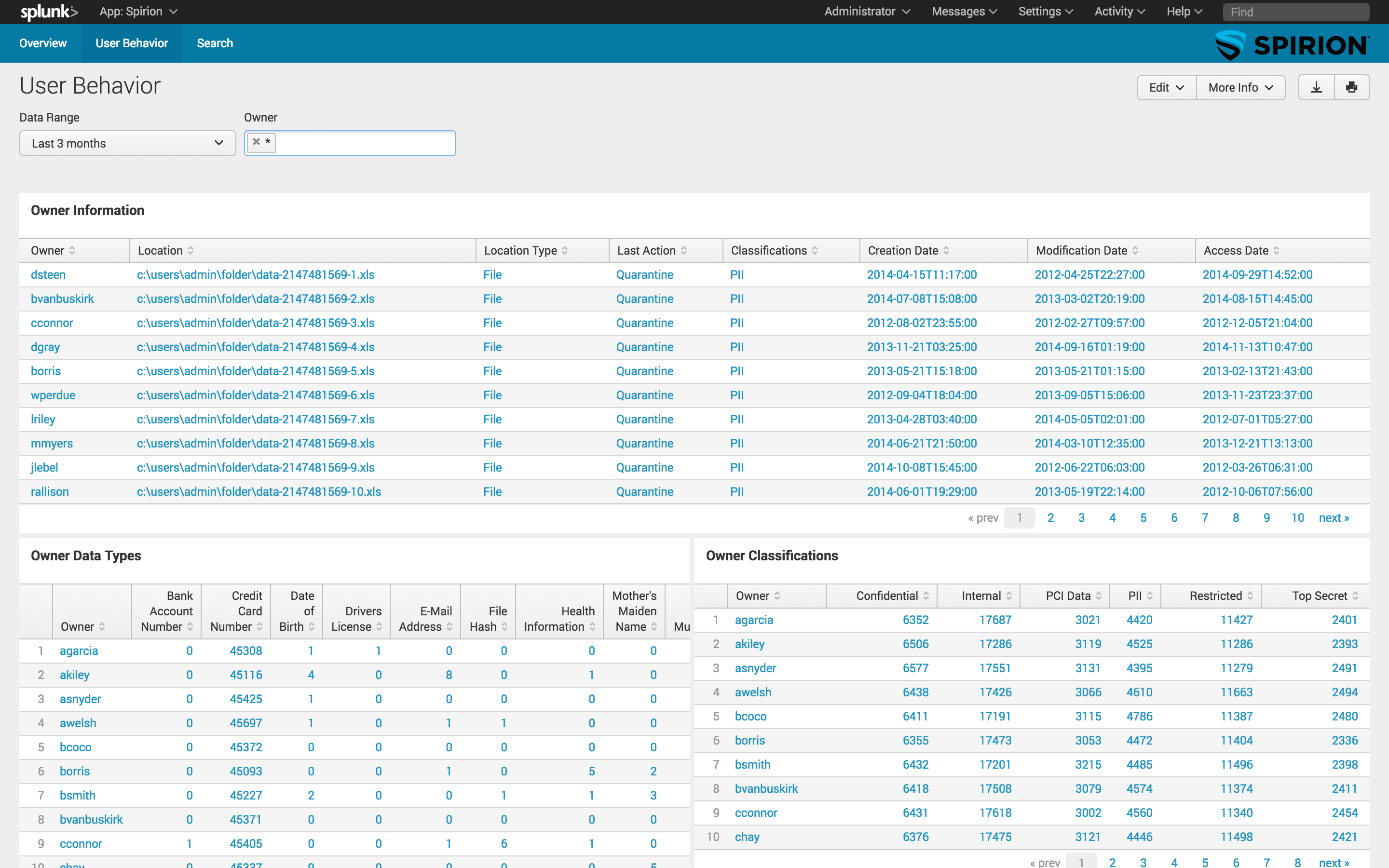
About the Spirion App for Splunk
Spirion is the leading provider of sensitive data risk reduction solutions. Spirion's enterprise solution accurately finds all sensitive data, anywhere, anytime and in any format on endpoints, servers, file shares, databases and in the cloud with practically zero false positives. The software eliminates and prevents sensitive data sprawl and the integration with Splunk lets customers understand and manage their risks in the context of all their other information security and business data.
Spirion's integration with Splunk enables customers to share, analyze, and correlate Spirion's sensitive data results with their existing enterprise security systems. Replacing costly and complex third party development integration and manual data exports, the Spirion integration allows endpoints and locations to be queried by Splunk to show the amount of sensitive data each holds and the amount of data that is currently unprotected. This allows companies to quickly and easily identify where they have data breach exposure.
This product contains the Add-on which integrates Spirion sensitive data events and alerts into Splunk Enterprise. The Add-on is designed for Spirion 10.0 and above. For use with previous versions please contact Spirion.
Release Notes
About this release
Version 1.0 of the Spirion App for Splunk is compatible with:
Support and resources
Support
Installation and Configuration
Hardware and Software Requirements
Hardware Requirements
Spirion App for Splunk supports the following server platforms in the versions support by Splunk Enterprise:
Software Requirements
To function properly, Spirion App for Splunk requires the following software:
Splunk Enterprise System Requirements
Because this add-on runs on Splunk Enterprise, all of the Splunk Enterprise system requirements apply.
Download
Download the Spirion App for Splunk at https://splunkbase.splunk.com/app/3312/
Installation steps
To install and configure this app on your supported platform, follow these steps:
Using the Web Interface:
Using the configuration files:
Standalone Splunk Environemnts and Independent Search Heads
Install the Spirion App for Splunk on the single server using one of the methods described above.
Distributed Environments
In distributed environments, the Spirion App for Splunk Enterprise should be installed on the search heads.
Configuration:
By default, the data gathered by the Spirion Technology Add-On indexes into the main index, and thus the dashboards in the Splunk app for Spirion assumes the same in its searches. If you plan to use a custom index, simply edit the spirion_index macro to reflect your new index name. This can be achieved by either creating a local copy of the macros.conf file within the app, or editing the macro through the UI by navigating to Settings>Advanced Search>Search macros. All that needs to be updated is the index definition for where the Spirion data will be sent.
As a Splunkbase app developer, you will have access to all Splunk development resources and receive a 10GB license to build an app that will help solve use cases for customers all over the world. Splunkbase has 1000+ apps from Splunk, our partners and our community. Find an app for most any data source and user need, or simply create your own with help from our developer portal.